IcedID is a new player in the banking Trojan family. It has a modular architecture and capable of stealing banking credentials of the user by performing a man-in-the-middle attack (MITM). IcedID sets up a local proxy and redirects all Internet traffic through it. Additionally, it can download and execute components required for stealth.
Infection vector
Normally, IcedID spreads through spam email or dropped by other malware families. In our analysis, we found the family to be Emotet. In early 2017, Emotet was widely used to spread other banking Trojans such as Qkabot and Dridex.
IcedID contains a network spreading module which is rarely observed in other banking Trojans. Looking at the API sequence in IcedID, it has adopted similar techniques which were successfully used by malware such as BadRabit, Petya/Not-Petya.
Analysis of sample
On execution, the sample drops a copy of itself on to the folder %LOCAL_APPDATA% with a random name in a randomly named folder. The name of the dropped file and folder is the same and contains 9 characters. The name of the dropped file is generated using a security identifier (SID) of the current user. Below is the code that generates the SID for the current logged on user.
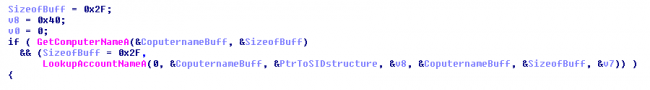
The name of the dropped file with a random name in a randomly named folder.
“%LOCALAPPDATA%\[a-z]{9}\[a-z]{9}.exe”
Example: –
“C:\Documents and Settings\Administrator\Local Settings\Application Data\homatluna\homatluna.exe”
It maintains its persistence by creating a registry entry in “Run”.
“HKCU\Software\Microsoft\Windows\CurrentVersion\Run\homatluna”
Next IcedID writes a RSA crypto-key to the system into the AppData folder. It then writes a certificate file in %TEMP% folder.
Example – “C:\Documents and Settings\Administrator\Local Settings\Temp\0137194B.tmp”
Network activity
It creates two socket connections. One for local proxy and another to serve as a backdoor for CnC communication. In our analysis, the port with the local proxy bind is 49158 and the backdoor is created on port number 49161.
It creates a local proxy. Using certificates of different banks and custom module, it implements its own SSL layer. Using this it performs MITM. IcedID can intercept all traffic and extract user credentials from it.
Once the malware enters the system, it sends the bot ID and basic system information to the CnC server through the POST request as seen in Fig 1 and Fig 2.
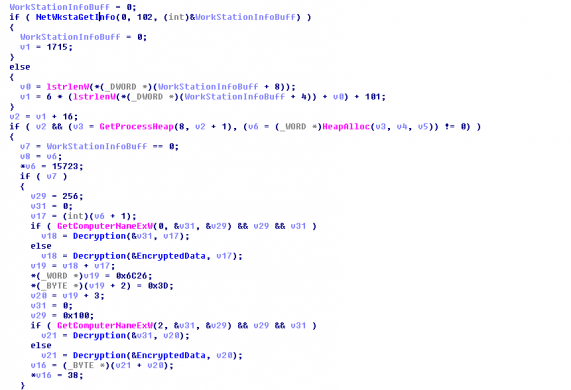
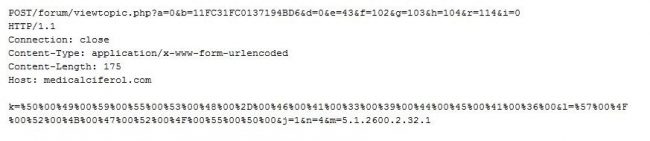
Following is the decoded post request details to be sent:
K – System Name
B – BOT ID
L – Work Group
M – OS Version
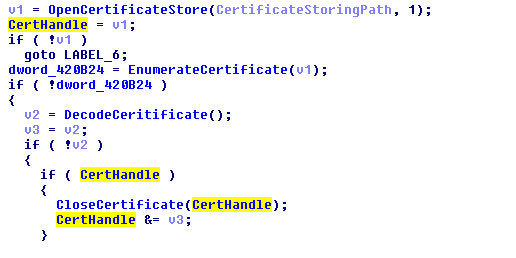
IcedID’s communication with CnC takes place over an encrypted SSL whose certificate is decided by the malware itself from the certificate store. The temp file which is dropped by the malware is used to store the certificate. The below code is used for certificate enumeration.
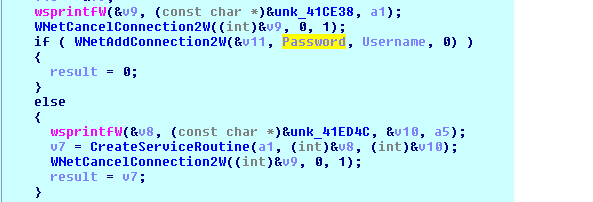
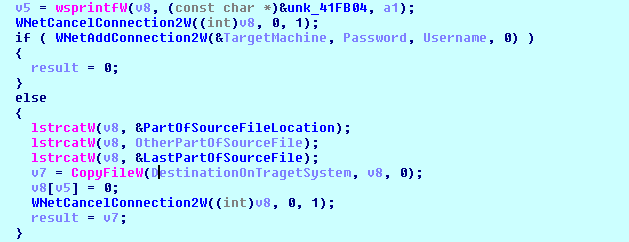
Spreading in the network
IcedID is different from other banking Trojans because it can spread within the network. It first finds the live system on the local network and copies itself on to the new system.
Indicator of compromises
csuwbru[.]net
comeontrk[.]com
medicalciferol[.]com
38921f28bb74fea2cab6e70039ee65f3
d982c6de627441765c89da5cfeb04d6f
82d6e69df2277073d4aaacd6994ee033
Quick Heal successfully detects IcedID as Trojan.IcedID.
The malware’s spreading behavior makes it more aggressive than the previously seen banking Trojans.
Prevention tips
- Install an antivirus and keep it updated.
- Keep your Operating System and software up-to-date.
- Do not click on links or download attachments from unknown, unexpected or unwanted sources.
Subject Matter Expert
Piyush Bansal | Ghanshyam More, Quick Heal Security Labs




