Just like any other business, cybercriminals run their syndicate with the sole aim of maximizing profits. With that in mind, let us decipher the role of AI in cybercrime to rethink their business operating model.
Shift in Targeted Cyber Attacks
Ever since Advanced Targeted Cyber Attacks became an organized business for profit, these attacks were mostly directed at Large Enterprises. That is because planning, preparing, and executing a targeted attack campaign is resource resource-intensive undertaking and requires substantial time and capital investment for the Attacker Group. Therefore, concentrating on high-value targets represented by Larger Enterprises made good business sense.
Changing Cyber-Attack Landscape
However, since around a decade ago, the cyber-attack landscape started to shift. More and more, advanced cyberattacks started targeting smaller organizations.
The reason for this trend can be substantially attributed to AI and Machine Learning technologies proliferating cyber defense.
Increase in Cybersecurity Spending
The chart below shows the trend in average spend on high-end cybersecurity tools by Large Enterprises for defense against advanced cyber threats:
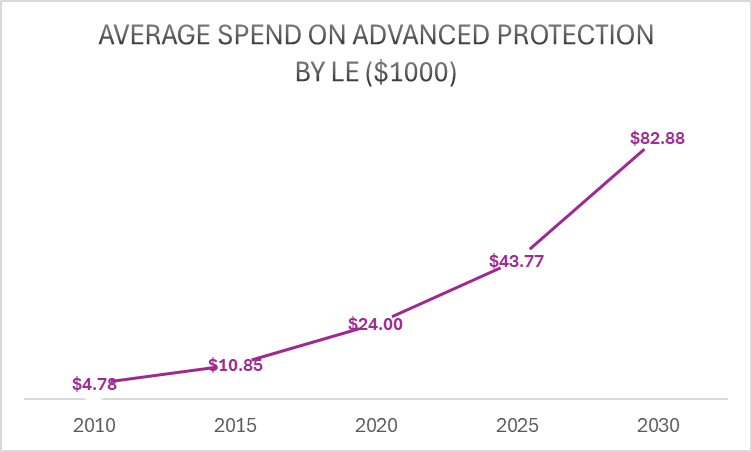
More and more advanced Behavior-based detection platforms such as next-generation SIEMs, have made the detection, response, and prevention of cyber-attacks much more effective.
Vulnerability of Smaller Organizations
Unfortunately, due to the prohibitively high cost of licensing and operation of SIEMs, these are largely out of reach of smaller organizations. And so, the smaller organizations have remained more vulnerable to Advanced attacks.
Shift in Cybercriminal Targets
Soon, Threat Actors, seeing the diminishing returns from attacking Large Organizations, turned to SMBs to stay in business, which was an easy target.
There was still one problem for the cybercriminal – the cost of launching an attack – zero-day exploits or compromised credentials that had to be purchased on the dark web were still quite expensive.
The below chart shows the average price of a specific zero-day exploit type sourced from the dark web compiled over some years and extrapolated.
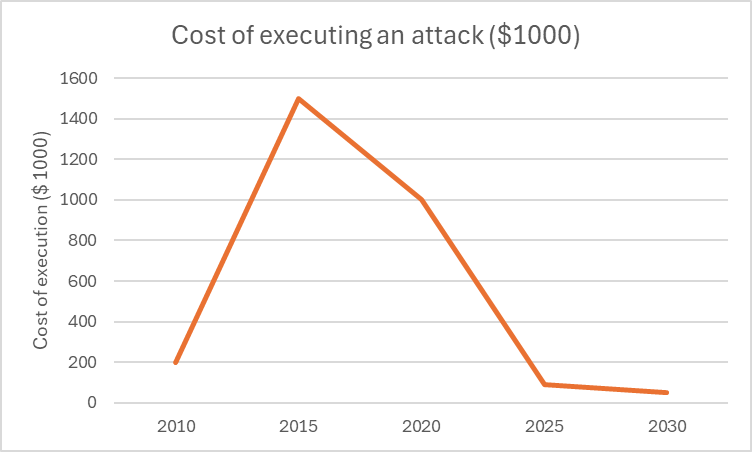
Reducing Cost of Attacks
Since the average profit to be made from compromising a single SMB is low, the overall profit from attacks on Small Businesses remained relatively low.
However, with the explosion of new AI-driven techniques of malware and exploit kit generation, this cost is going to drastically reduce in the upcoming decade. As such, this will lead to a huge increase in advanced attacks targeting smaller organizations.
Implications for SMBs
The chart below shows the percentage of cyberattacks targeting SMBs extrapolated till 2030:
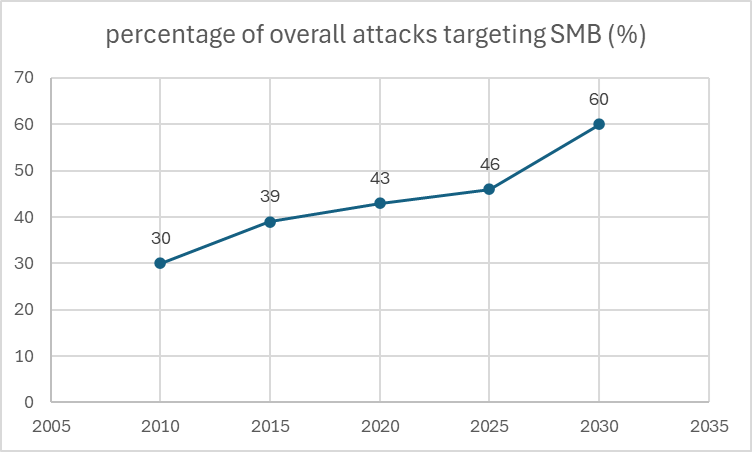
As a Small or Midmarket organization, this should be troubling news for you. A single cyberattack led to the compromise of your assets often leads to business closure due to the monetary and reputation impact.
AI-Driven Cybersecurity Solutions
Fortunately, help is at hand and it’s AI once again. The new breed of cybersecurity tools, led by XDR, or more appropriately, next-gen AI-driven XDRs or AI-XDRs in short, whose primary focus is small and mid-market organizations, can bridge the cyber defense gap for the SMB. AI-XDRs are relatively low-priced alternatives for the expensive SIEM, coming in at a third to a fifth of the price, and provide exceptional protection against advanced attacks, while also fulfilling all the regulatory needs that a SIEM brings. The primary focus of AI-XDR is automated advanced attack detection and response. They depend heavily on AI for detection and automated response and almost completely do away with the need for in-house high-end Security Analysts for Incident Response. Combined with precise Threat Intelligence from relevant regional and vertical-specific sources, the purpose-built AI-XDR can ensure smaller organizations are well prepared to repel the onslaught of Advanced attacks that are already targeting these organizations and are going to increase tremendously soon.




