Overview
Seqrite Labs, India’s largest Malware Analysis lab, has identified multiple cyber events linked to Operation Sindoor, involving state-sponsored APT activity and coordinated hacktivist operations. Observed tactics included spear phishing, deployment of malicious scripts, website defacements, and unauthorized data leaks. The campaign exhibited a combination of cyber espionage tactics, hacktivist-driven disruptions, and elements of hybrid warfare. It targeted high-value Indian sectors, including defense, government IT infrastructure, healthcare, telecom, and education. Some of the activities were attributed to APT36 and Sidecopy, Pakistan-aligned threat groups known for leveraging spoofed domains, malware payloads, and credential harvesting techniques against Indian military and government entities.
Trigger Point: Initial Access Vector
On April 17, 2025, Indian cyber telemetry started to light up. Across the threat detection landscape, anomalies directed towards government mail servers and defence infrastructures. Lure files carried names that mimicked urgency and legitimacy:
- xlam
- ppam
- pptx.lnk
These weren’t ordinary files. They were precision-guided attacks—documents laden with macros, shortcuts, and scripts that triggered covert command-and-control (C2) communications and malware deployments. Each lure played on public fear and national tragedy, weaponizing recent headlines like the Pahalgam Terror Attack. Further technical details can be found at :
- Advisory: Pahalgam Attack themed decoys used by APT36 to target the Indian Government
- Umbrella of Pakistani Threats: Converging Tactics of Cyber-operations Targeting India | Seqrite
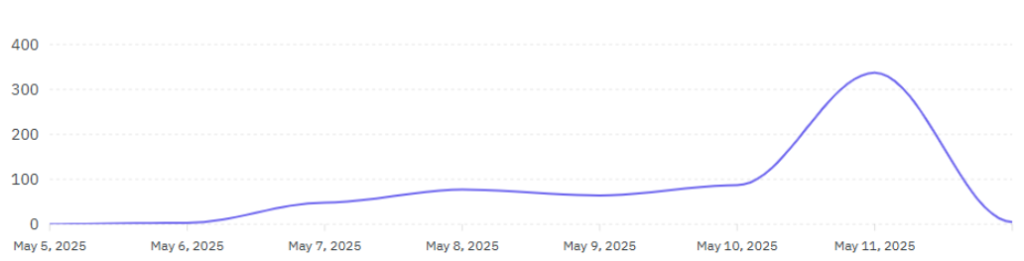
Following the initiation of Operation Sindoor on May 7th, a surge in hacktivist activities was observed, including coordinated defacements, data leaks, and disruptive cyber campaigns.
Activity Timeline Graph – Operation Sindoor
APT36: Evolution of a Digital Predator
APT36, long associated with the use of Crimson RAT and social engineering, had evolved. Gone were the older Poseidon loaders—Ares, a modular, evasive malware framework, now formed the new spearhead.
Tools & File Types:
- .ppam, .xlam, .lnk, .xlsb, .msi
- Macros triggering web queries:
fogomyart[.]com/random.php - Payload delivery through spoofed Indian entities:
zohidsindia[.]com, nationaldefensecollege[.]com, nationaldefencebackup[.]xyz - Callback C2 IP: 167.86.97[.]58:17854(Crimson RAT C2).
APT36 used advanced TTPs during Operation Sindoor for stealthy infection, persistence, and command and control. Initial access was via spear phishing attachments (T1566.001) using malicious file types (.ppam, .xlam, .lnk, .xlsb, .msi). These triggered macros executed web queries (T1059.005) to domains like fogomyart[.]com. Payloads were delivered through spoofed Indian domains such as zohidsindia[.]com and nationaldefensecollege[.]com, with C2 communication via application layer protocols (T1071.001) to 167.86.97[.]58:17854. For execution and persistence, APT36 leveraged LOLBins (T1218), scheduled tasks (T1053.005), UAC bypasses (T1548.002), and obfuscated PowerShell scripts (T1059.001, T1027), enabling prolonged access while evading detection.
Ares RAT grants full control over the compromised host, offering capabilities such as keylogging, screen capturing, file manipulation, credential theft, and remote command execution—similar to commercial RATs but tailored for stealth and evasion.
Digital Infrastructure: Domains of Deception
The operation’s domain arsenal resembled a covert intelligence operation:
- pahalgamattack[.]com
- operationsindoor2025[.]in
- sindoor[.]website
- sindoor[.]live
These domains mimicked military and government entities, exploiting user trust and leveraging geo-political narratives for social engineering.
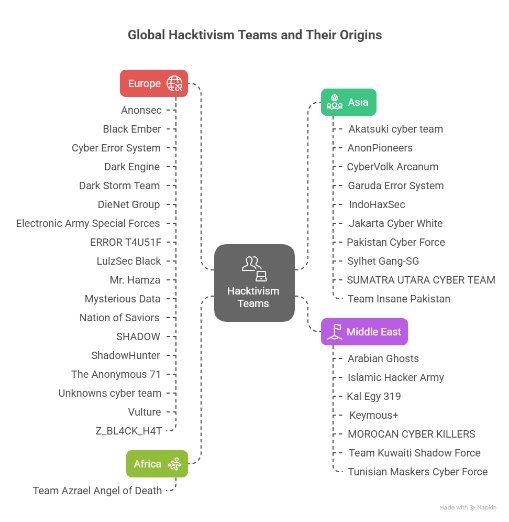
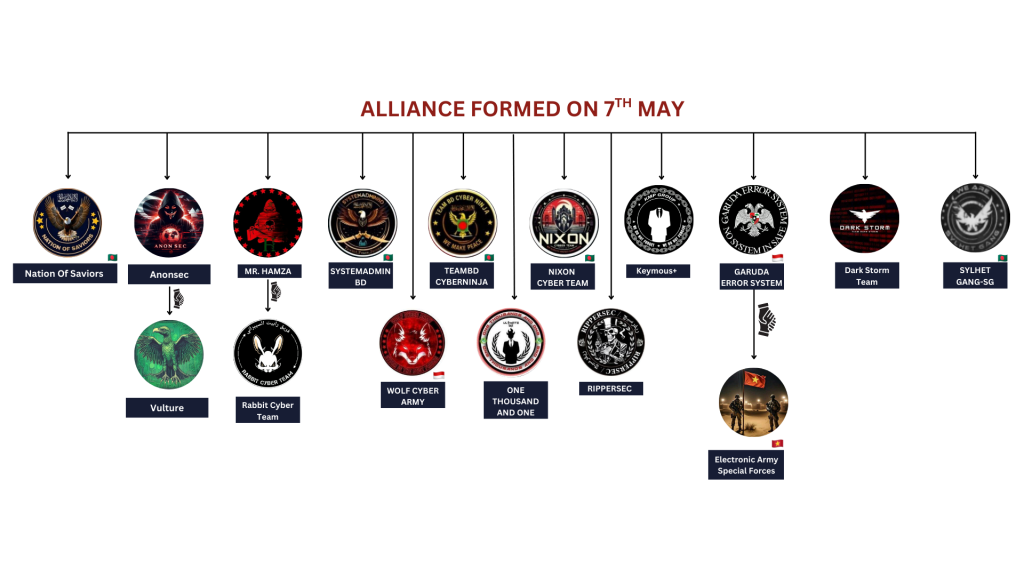
Hacktivism in Tandem: The Shadow Battalion
APT36 did not act alone. In parallel, hacktivist collectives coordinated disruptive attacks—DDoS, defacements, and data leaks—across key Indian sectors. Telegram groups synchronized actions under hashtags like #OpIndia, #OperationSindoor, and #PahalgamAttack, as portrayed in the image below.
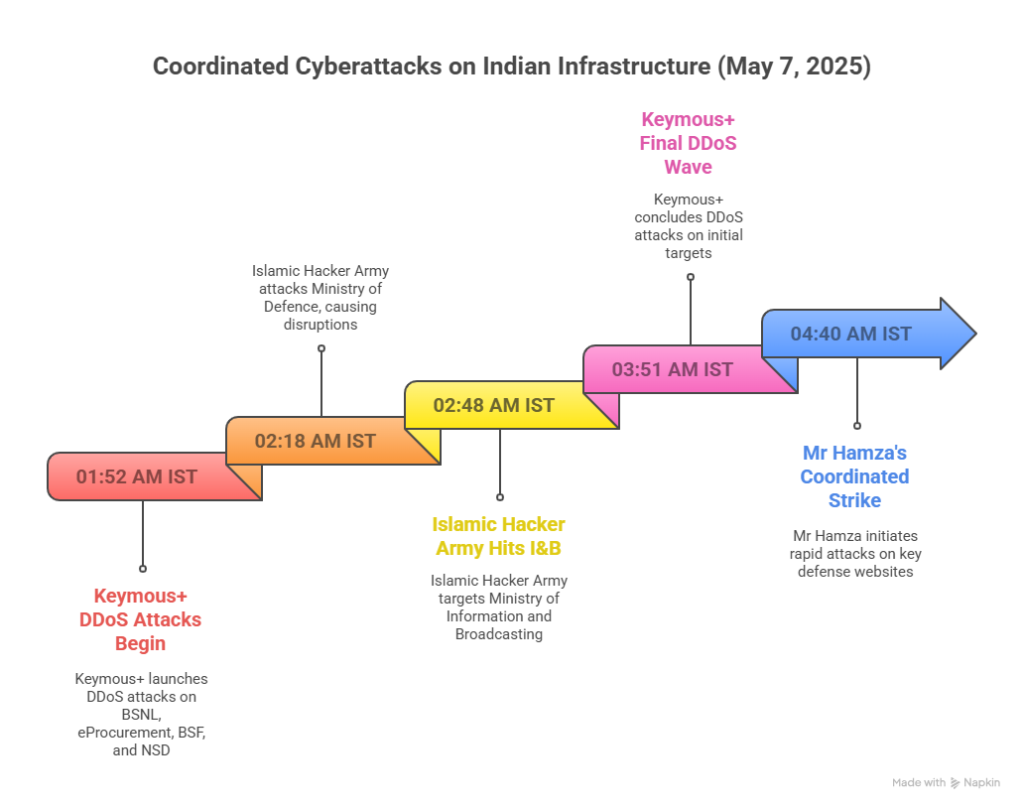
Most Targeted Sectors:
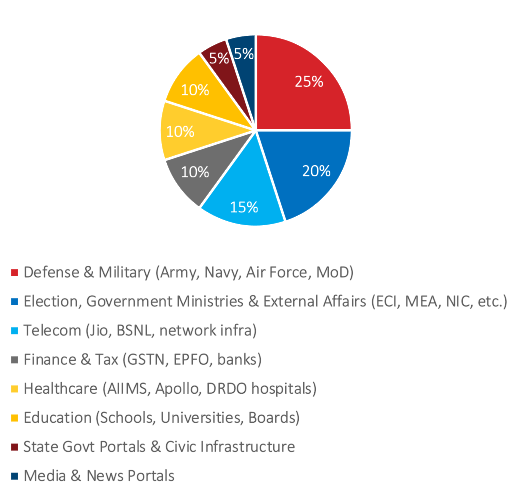
The Operation Sindoor campaign strategically targeted India’s critical sectors, focusing on Defense entities like the MoD, Army, Navy, and DRDO. The hactivists claimed to have disrupted Government IT infrastructure, including NIC and GSTN with evidences of DDoS and data leak, while attempting breaches in healthcare institutions such as AIIMS and DRDO Hospitals. Telecom giants like Jio and BSNL were probed, alongside multiple state-level educational and government portals, showcasing the breadth and coordination of the cyber offensive.
Post-Campaign Threat Landscape
From May 7–10, Seqrite telemetry reported:
- 650+ confirmed DDoS/defacement events
- 35+ hacktivist groups involved, 7 newly emerged
- 26 custom detection signatures deployed across XDR
Detection Signatures:
| Signature Name | Description |
| BAT.Sidecopy.49534.GC | SideCopy loader script |
| LNK.Sidecopy.49535.GC | Macro-enabled shortcut |
| MSI.Trojan.49537.GC | MSI-based Trojan dropper |
| HTML.Trojan.49539.GC | HTML credential phisher |
| Bat.downloader.49517 | Download utility for RAT |
| Txt.Enc.Sidecopy.49538.GC | Obfuscated loader |
IOCs: Indicators of Compromise
Malicious Domains:
- pahalgamattack[.]com
- sindoor[.]live
- operationsindoor2025[.]in
- nationaldefensecollege[.]com
- fogomyart[.]com/random.php
Malicious Files:
- xlam
- ppam
- pptx.lnk
Callback IP:
- 167.86.97[.]58:17854(Crimson RAT C2)
VPS Traffic Origination:
- Russia 🇷🇺
- Germany 🇩🇪
- Indonesia 🇮🇩
- Singapore 🇸🇬
The Mind Map of Chaos: Coordinated Disruption
Seqrite’s Response
To counteract the operation, Seqrite Labs deployed:
- 26 detection rules across product lines
- YARA signatures and correlation into STIP/MISP
- XDR-wide alerting for SideCopy and Ares variants
- Dark web and Telegram monitoring
- Threat advisory dissemination to Indian entities
Researcher’s Reflection
Operation Sindoor revealed the blueprint of modern cyber warfare. It showcased how nation-state actors now collaborate with non-state hacktivists, merging technical intrusion with psychological operations. The evolution of APT36—especially the move from Poseidon to Ares—and the simultaneous hacktivist attacks signal a deliberate convergence of cyber espionage and ideological warfare.
Instead of isolated malware campaigns, we now face digitally coordinated war games. The tools may change—macros, MSI files, DDoS scripts—but the objectives remain: destabilize, disinform, and disrupt.
Conclusion
Operation Sindoor represents a significant escalation in the cyber conflict landscape between India and Pakistan. The campaign, orchestrated by APT36 and allied hacktivist groups, leveraged a blend of advanced malware, spoofed infrastructure, and deceptive social engineering to infiltrate key Indian sectors.
The strategic targeting of defense, government IT, healthcare, education, and telecom sectors underscores an intent to not just gather intelligence but also disrupt national operations. With the deployment of tools like Ares RAT, attackers gained complete remote access to infected systems—opening the door to surveillance, data theft, and potential sabotage of critical services.
From an impact standpoint, this operation has:
- Undermined trust in official digital communication by spoofing credible Indian domains.
- Increased operational risks for sensitive departments by exposing infrastructure weaknesses.
- Compromised public perception of cybersecurity readiness in government and defense.
- Amplified geopolitical tension by using cyber means to project influence and provoke instability.
The impact of this campaign on national cybersecurity and trust has been significant:
- Data Exfiltration: Sensitive internal documents, credentials, and user information were exfiltrated from key organizations. This compromises operational security, strategic decision-making, and opens pathways for follow-up intrusions.
- DDoS Attacks: Targeted denial-of-service attacks disrupted availability of critical government and public-facing services, affecting both internal workflows and citizen access during sensitive geopolitical periods.
- Website Defacement: Several Indian government and institutional websites were defaced, undermining public confidence and serving as a psychological warfare tactic to project influence and cyber superiority.
These developments highlight the urgent need for enhanced threat intelligence capabilities, robust incident response frameworks, and strategic public-private collaboration to counter such evolving hybrid threats.




