AI-Driven Cybersecurity on a Single, Unified Platform

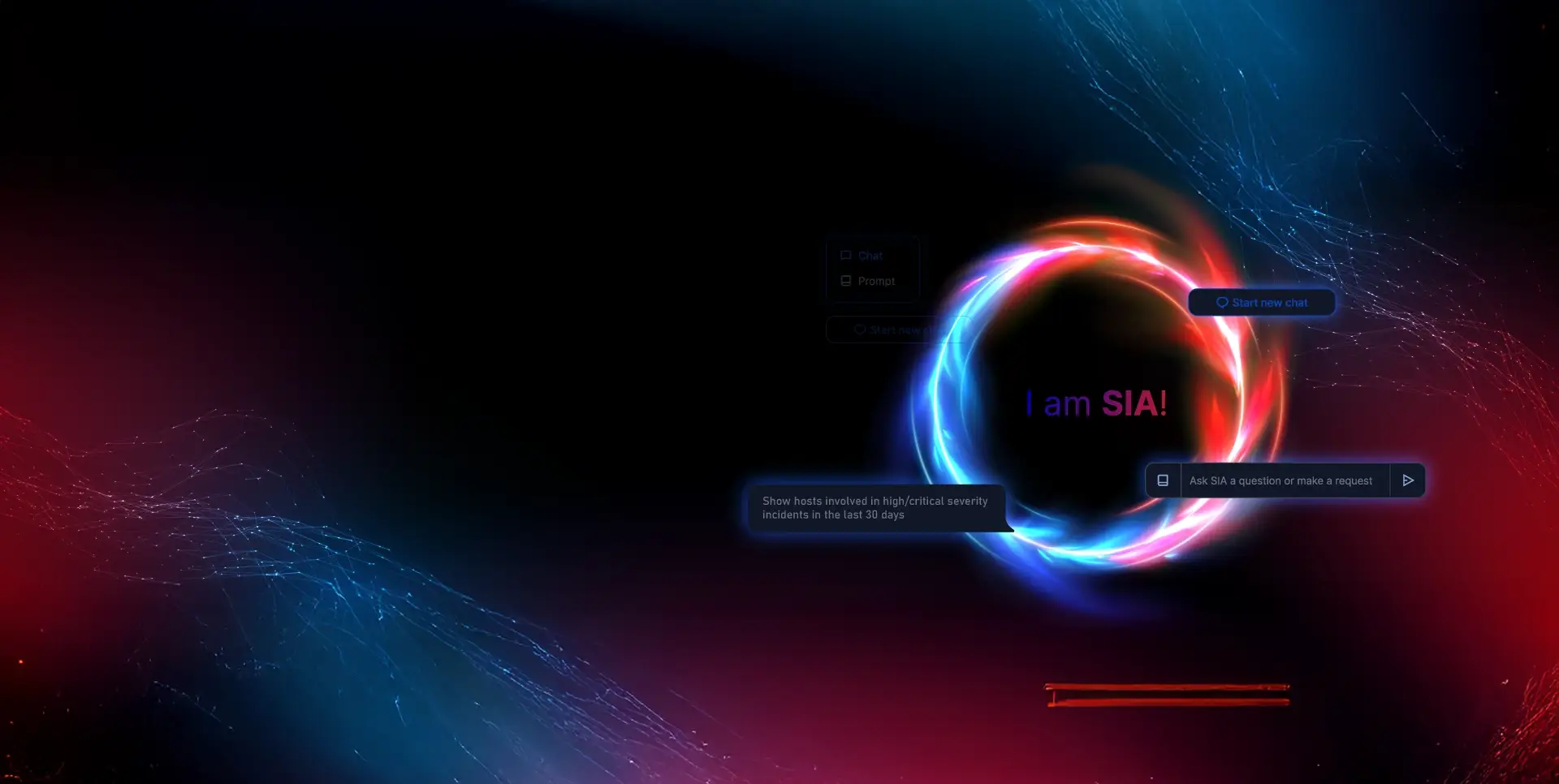
SIA - Your Virtual AI Security Analyst
Harness the Power of Gen AI to Simplify Security and Accelerate Response. Cut through the noise. SIA automates routine tasks, delivers instant insights, and helps security teams act faster—all through simple, natural language. Reduce complexity, boost efficiency, and stay ahead of threats with GenAI on your side.
Know MoreWe Protect Your Organization Anywhere, Anytime
Seqrite delivers AI-driven protection across endpoints, networks, cloud, and hybrid environments—helping organizations confidently manage today’s complex threat landscape without fragmented tools or alert fatigue.
Endpoint Protection
Experience AI-powered endpoint protection to stop advanced threats across your endpoints with ease and confidence.

Endpoint Detection and Response
Proactively defend your enterprise endpoints against sophisticated cyberattacks to prevent data breaches, minimize downtime, and enhance your overall security posture.
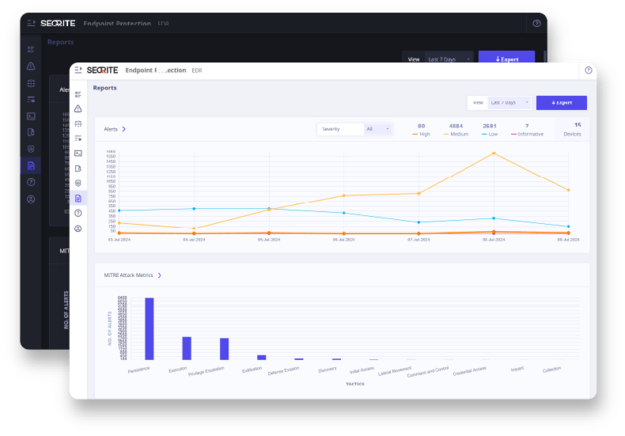
Extended Detection and Response
Leverage automated detection and response capabilities to effectively neutralize sophisticated threats with speed and precision.
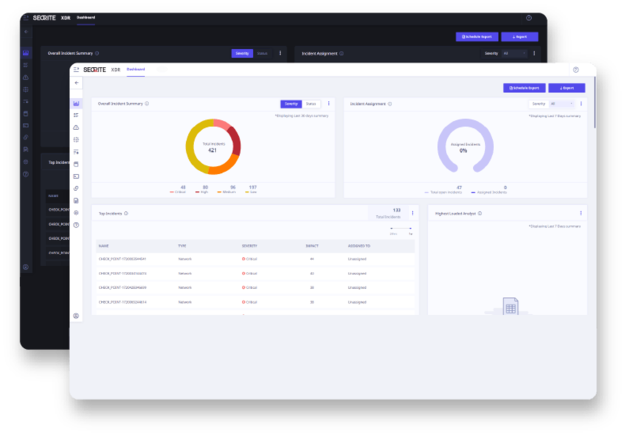
Zero Trust Network Access
Enhance enterprise security by enforcing zero-trust principles to safeguard your modern workforce while ensuring complete visibility of user activity.
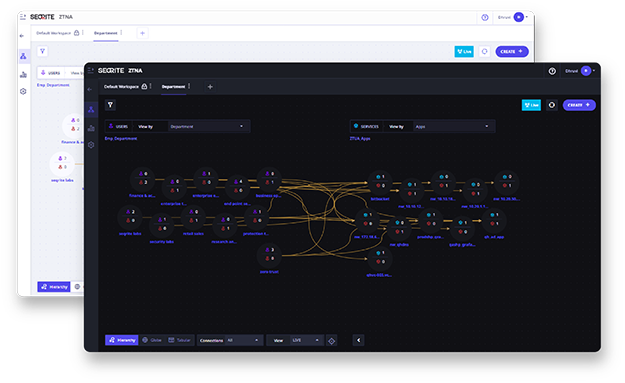
Data Privacy
Discover and manage sensitive data to ensure compliance with data privacy regulations while building and enhancing customer trust.
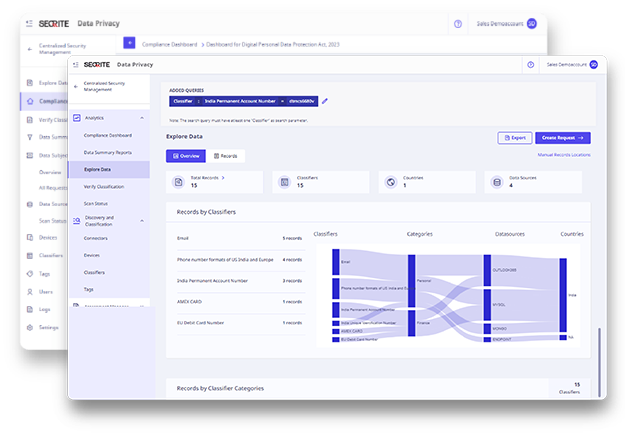
Mobile Device Management
Streamline enterprise app management and enforce policies across company-owned Android and iOS devices while ensuring complete security.
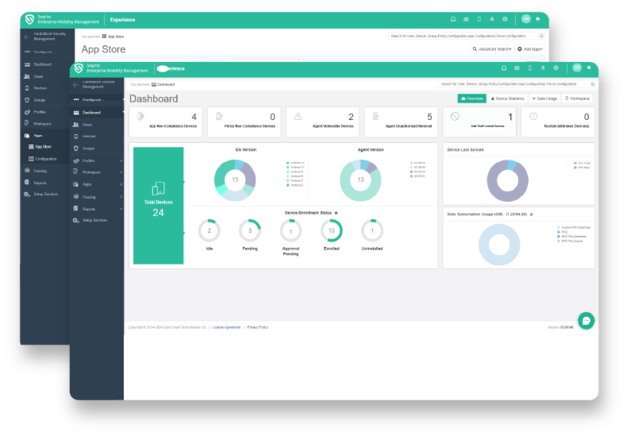
BYOD
Securely manage corporate data and applications on employee-owned devices without compromising on privacy.

Managed Detection and Response
Elevate your security operations with AI-powered threat detection, investigation, and response, seamlessly integrated with expert human insights to ensure comprehensive cyber protection.
Malware Analysis Platform
Detect, analyze, and neutralize advanced threats with deep insights, empowering your defense strategy through proactive malware detection.
Threat Intel
Leverage real-time, actionable threat intelligence for faster response and proactive defense with global and industry-specific insights.
SOHO Total Edition
Secure Your Small Office Like a Fortune 500 – Without the Cost or Complexity. Discover Seqrtire SOHO Total Edition.

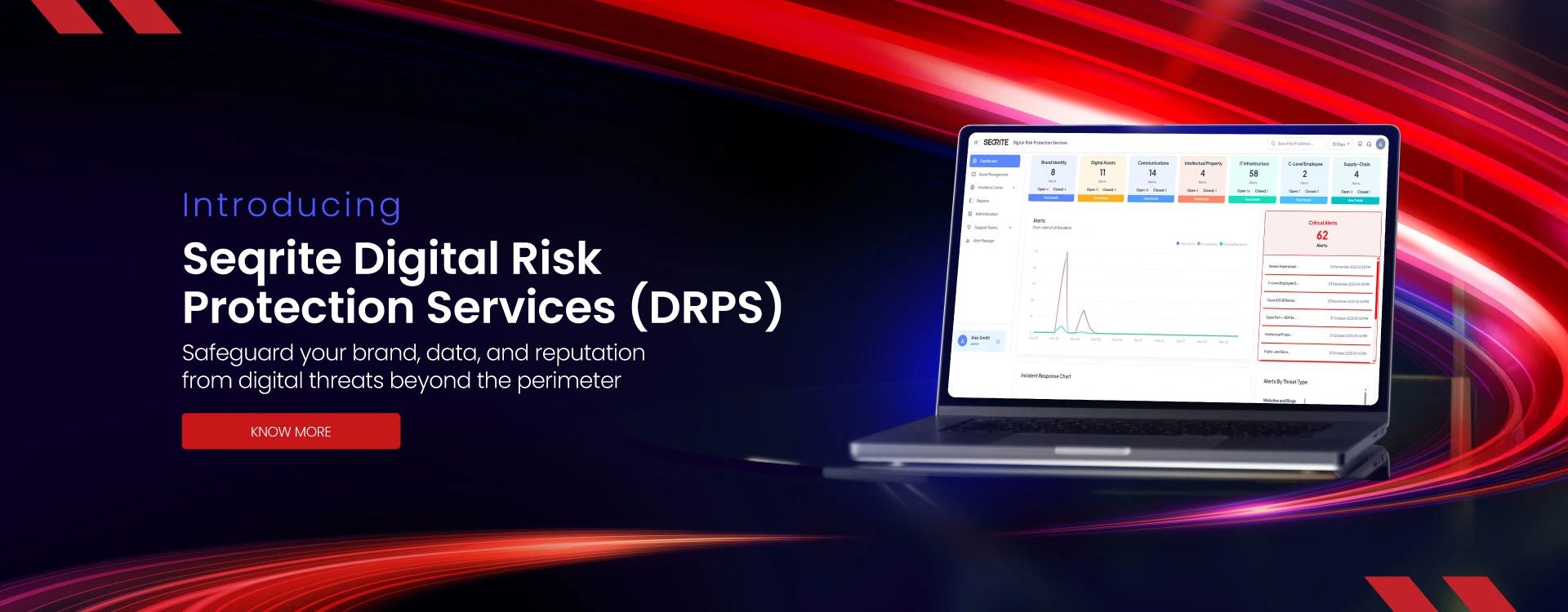
Digital Risk Protection Services (DRPS)
Safeguard your brand, data, and reputation from digital threats beyond the perimeter.
What Sets us Apart?
Flexible Cloud and On-Prem Solutions
Patented AI/ML-Driven Technology
Intel From One of the Largest Malware Lab
Robust On-Ground Customer Support
Single, Unified Security Platform
30+ Years of Security Expertise
1,000+ Cybersecurity Experts
Thought Leadership Edge
Testimonials
What our customers are saying
Contact our Cybersecurity Experts