An increasing volume of business information assets are distributed digitally today and has been growing exponentially every year. Confidential and sensitive business information is no longer restricted to physical boundaries of business enterprises. With the implementation of policies like cloud-based storage services and BYOD (Bring-Your-Own-Device) at the workplace, Data Loss Prevention (DLP) becomes an integral part of IT security for enterprises of all sizes.
One of the greatest challenges in managing data loss is that there are so many reasons why data loss can occur and enterprises do not have effective strategies in place to manage the problem. According to statistics, 31% of endpoint users have lost their data due to events beyond their control. In an organizational setup with multiple endpoint users, enterprise data can fall into the hands of outsiders either by transfers from web-based applications or via physical devices.
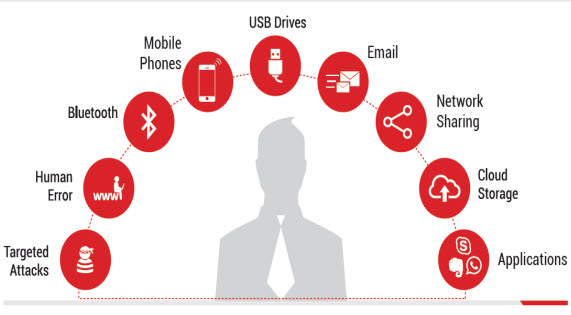
Seqrite Data Loss Prevention (DLP)
Seqrite Data Loss Prevention (DLP) is an electronic data supervision solution designed to help enterprises establish control over their data by preventing confidential data from being leaked out of an organization’s network. With Seqrite DLP, IT admins can enforce compliance measures and define security policies to establish control over the data transferred via physical devices or web applications.
Seqrite DLP enables IT admins to implement a multi-layered approach to data regulation and data security. The solution –
Monitors and Protects Sensitive Data: Stops data leakage within or outside the organization by regulating data transfer channels such as removable devices, network share, clipboard, print screen and printing activities on endpoints.
User-Defined Dictionaries: Allows IT admins to define phrases or keywords relevant to the data security requirements of enterprises and monitor them on endpoints. The feature safeguards intellectual property (IP) rights, copyright information or any type of data which the enterprise feels is sensitive and needs to be protected.
Data-At-Rest Scan: DLP proactively scans local drives, folders, and removable drives on endpoints for files containing confidential and sensitive data. Exclusion of specific folders from data-at-rest scan is allowed within DLP.
Notifications: Email notifications are sent whenever the data loss prevention policy is violated.
Domain and Network Exclusions: Allows IT admins to exclude internal domains, certain locations in a shared network, and applications from DLP monitoring and permits the exchange of confidential data/files among relevant stakeholders within the enterprise.
Proactive monitoring of applications, confidential data and files: Monitors various application types such as Instant Messengers, web browsers, social media, email clients and file sharing/cloud services; confidential data types such as credit/debit card numbers, PAN, SSN (Social Security Number), Corporate My Number, bank accounts etc., & file types such as programming files, graphic, multimedia files, compressed files, executable files and more.
Seqrite Data Loss Prevention (DLP) can be effectively combined with Advanced Device Control and File Activity Monitor for complete endpoint protection of enterprise data and is available with Seqrite Endpoint Security (EPS) editions – Business, Total and Enterprise Suite.
Seqrite helps businesses simplify IT security and maximize business performance. To know more about our products and services visit our website or




