Introduction
In August 2025, a Telegram channel named “Scattered LAPSUS$ Hunters” surfaced, linking itself to notorious cybercrime groups: Scattered Spider, ShinyHunters, and LAPSUS$. The group quickly began posting stolen data, ransom demands, and provocative statements, reviving chaos once driven by LAPSUS$. Its name hints at connections to “The Com”, an underground network where actors often share tools and identities, making attribution complex. As covered in our earlier blog on the Google-Salesforce breach, such overlaps are common among clusters like UNC3944 (Scattered Spider), UNC5537 and UNC6040.
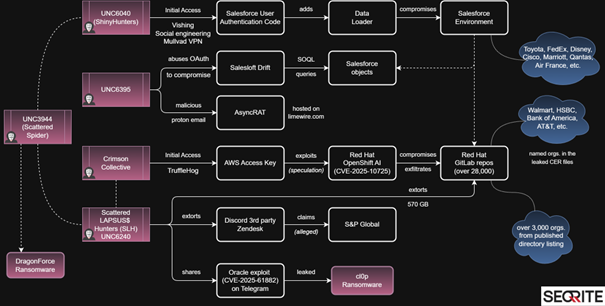
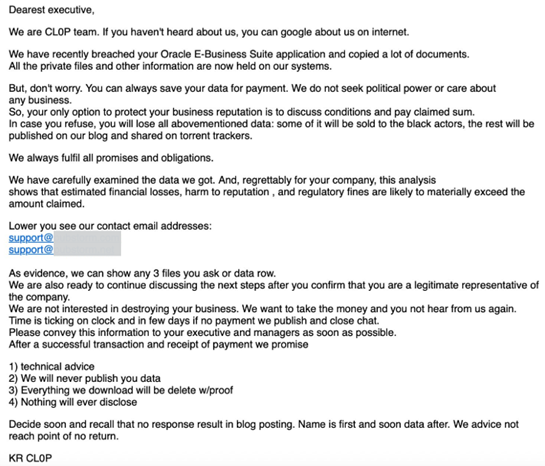
The Scattered LAPSUS$ Shiny Hunters (SLSH) group reportedly shared exploit code for CVE-2025-61882, a critical zero-day flaw in Oracle’s E-Business Suite that allows unauthenticated remote code execution. Oracle confirmed the issue and released an emergency patch after Mandiant revealed that the Clop ransomware group had exploited the flaw in August 2025 to steal data and conduct ransom campaigns. In September, hackers linked to SLSH breached a third-party provider for Discord, exposing limited user data, including payment details and IDs, and demanded ransom to prevent leaks. Evidence suggested access to Discord’s admin systems via a Zendesk compromise. Researchers believe ShinyHunters operates an Extortion-as-a-Service (EaaS) model, partnering with other hackers for ransom operations, an idea reinforced by other breaches. On October 11, SLSH announced plans to publicly launch its EaaS platform.
Threat Landscape
Recent posts threaten to leak Salesforce-related data if ransoms are unpaid by October 10 and hint at further attacks linked to the Salesloft ecosystem. Investigations indicate that the group relies heavily on vishing-based social engineering, convincing employees to install fake Salesforce Data Loader apps or approve malicious connected apps to gain access. These incidents underscore that the real weakness lies not in software flaws but in human manipulation, a persistent hallmark of this evolving threat landscape. Salesforce has publicly stated it will not comply with ransom demands made by the Scattered LAPSUS$ Hunters (SLH) group.
Shortly after this stance became public, a malware-laced message titled “Shiny hunters” was sent to KrebsOnSecurity, containing physical threats and a malicious link hosted on limewire[.]com. Similar threatening emails targeted Mandiant and several other security firms.
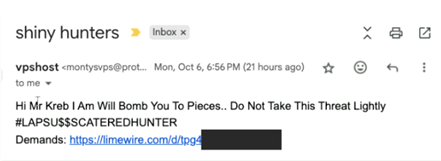
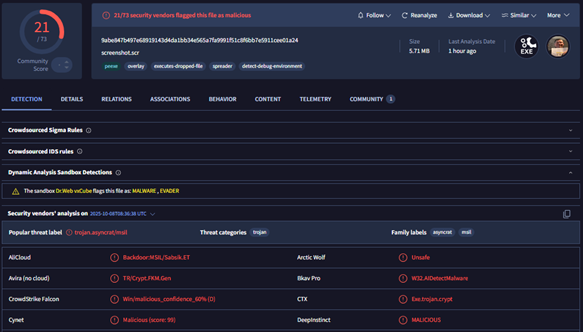
The link masqueraded as a screenshot file that secretly dropped a Remote Access Trojan (RAT), capable of surveillance, credential theft, and keylogging, without the victim opening the file. Mandiant later identified the malware as AsyncRAT, a .NET-based RAT widely used in cybercrime operations. Its plugin-based design allows attackers to quietly run malicious tools, capture screenshots, log keystrokes, and mine cryptocurrency.
Such intimidation tactics are consistent with past SLH behavior, where members targeted researchers and law enforcement investigating their campaigns. Meanwhile, law enforcement pressure is mounting. In late September, two suspected Scattered Spider members were arrested in the UK for stealing and extorting over $115 million through similar operations.
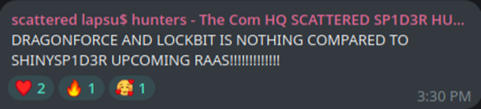
Despite multiple arrests over the years, these groups or their rebrands remain active and increasingly bold. They claim to operate a new ransomware service, “SHINYSP1D3R” , and sell exploits, though most of these claims remain unverified. Many alleged victims match past UNC5537 and UNC6040 targets, suggesting continuity rather than a new actor.
Oracle Zero-Day Exploitation
The Scattered LAPSUS$ Shiny Hunters (SLSH) group also appears to have shared exploit code CVE-2025-61882, a critical zero-day in Oracle’s E-Business Suite, allowing unauthenticated remote code execution i.e., it may be exploited over a network without the need for a username and password.
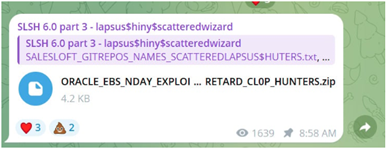
Oracle has verified and issued an emergency patch, urging customers to update immediately. Mandiant’s Charles Carmichael confirmed that the Clop ransomware group first exploited this flaw in August 2025 to steal data from Oracle servers and initiate ransom campaigns.
Exploit activity targeting Oracle EBS servers was observed as early as July 2025, prior to the release of official patches. Some of the exploit artifacts reportedly overlap with an exploit shared in the SLSH Telegram channel on October 3, 2025. However, GTIG (Google Threat Intelligence Group) notes that there is insufficient evidence to conclusively attribute the core intrusion to SLH or “Shiny Hunters” (UNC6240).
Red Hat and Discord Breach
On September 20, hackers breached a third-party support provider used by Discord, stealing user identities, payment info, and government-issued IDs from a limited number of users who interacted with customer support or Trust & Safety.
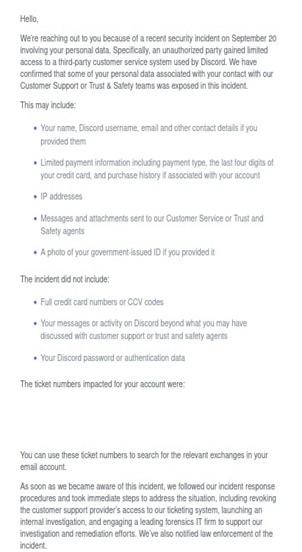
First seen in September 2025 by Rapid7, the group uses TruffleHog, an open-source tool, to scan for leaked AWS credentials. Once access is gained, they create new users, escalate privileges, and exfiltrate databases, project repos, and EBS snapshots using native AWS services like S3 and RDS.
They often deploy custom EC2 instances with permissive security groups, attach stolen volumes, and use Simple Email Service (SES) or external accounts to send extortion emails to victims. The group’s tactics show careful planning, high automation, and a focus on cloud-native abuse — all while leveraging valid credentials, not exploits.
Although their exact structure remains unclear, the use of shared IPs and language in ransom notes suggests multiple actors are involved. Their focus appears to be data theft over encryption, aligning them more with modern extortion-as-a-service operations.
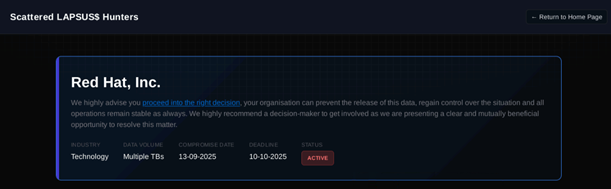
There is growing speculation that the Red Hat compromise may be linked to a recently disclosed vulnerability in Red Hat OpenShift AI — CVE-2025-10725 (CVSS 9.9). While no official attribution has been made, but we observed that the sample data leaked by Scattered LAPSUS$ Shiny Hunters (SLSH) contained .config and .yml files referencing internal infrastructure details. This suggests that Crimson Collective may have exploited the vulnerability as part of their access or escalation strategy within the compromised environment. According to Red Hat, the flaw requires minimal authentication and allows a low-privileged user to escalate privileges and gain cluster administrator access, potentially compromising all workloads and data within the hybrid cloud environment.
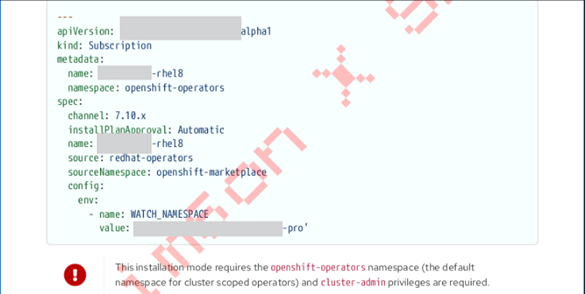
This serious vulnerability threatens the confidentiality, integrity, and availability of the entire AI platform. OpenShift AI, Red Hat’s enterprise-grade solution for managing AI/ML workloads at scale, is widely used across industries and integrates tools like Jupyter notebooks, making the impact of such a flaw potentially far-reaching.
IP addresses linked to this activity by Rapid7 were primarily used for port-scanning activity. Targeted ports are 9, 21, 80, 81, 82, 443, 3000, 3001, 4443, 5000, 5001, 7001, 8000, 8008, 8010, 8080, 8081, 8082, 8443, 8888, 9000, 9001, 9090, 9091, 9099. Activity for these IPs was observed between 8th and 20th September.
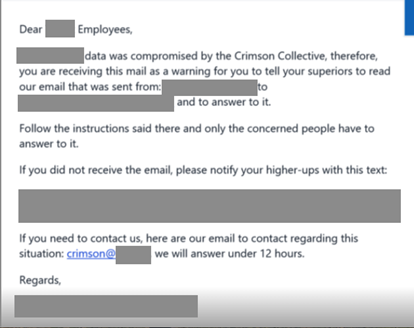
Later, researchers observed that Scattered Lapsus$ Shiny Hunters (SLSH) listed Red Hat on their leak site — indicating that SLSH is extorting Red Hat on behalf of Crimson Collective. Analysts now believe the Red Hat data breach is likely a collaborative operation between SLSH and Crimson Collective.
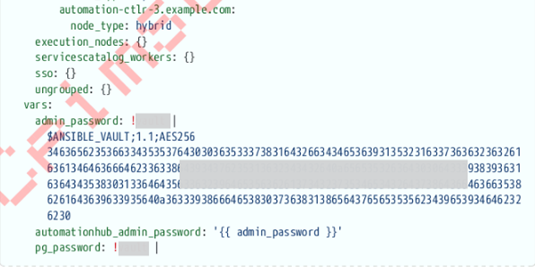
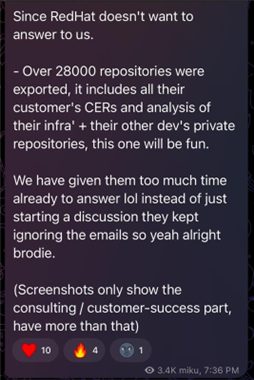
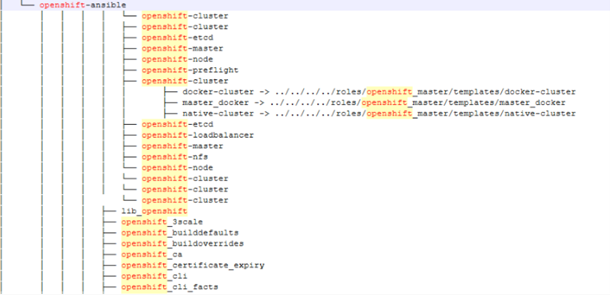
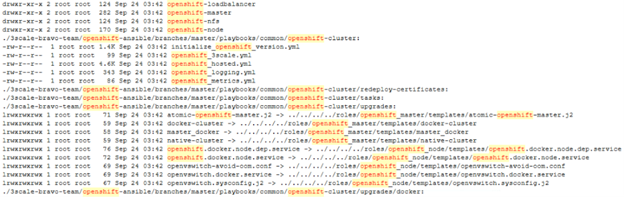
An analysis of the file tree and data samples shared by Crimson Collective—and later referenced on the Scattered LAPSUS$ Hunters leak site—indicates that numerous organizations may be impacted by the Red Hat breach. The names of companies and environments included in the leaked repository structure suggest a wide operational footprint. While the actual file contents remain inaccessible, the naming conventions and structure provide insight into the possible reach of the compromise. Some of the sample CER dataset shared in the leak site revealed example configuration scripts (.cfg, .yml), example authentication tokens, sample network diagrams and default passwords. Even when labelled “examples”, these files could pose risk to customers (who appear in those CER files) if they come directly from production-like engagements.
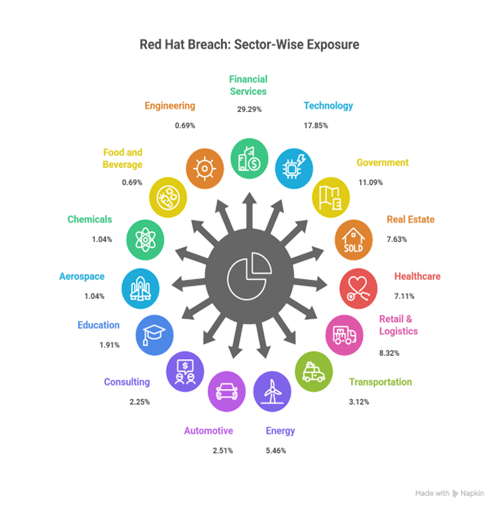
It’s important to note that the following statistical chart is based solely on directory tree and file names, which we observed in their leaked sample data structure. Since the underlying files or data were not accessible, we cannot say with complete certainty that all entries reflect active or legitimate systems, some entries may reflect outdated systems, internal testing, or incomplete deployments. However, the extensive listing—covering nearly five years of consulting activities—strongly suggests that a significant portion of this information may relate to real, deployed production environments across the listed organizations.
Analysis based on the Red Hat leaked directory tree shows that BFSI happens to be the most affected sector (~29%), followed by technology (~17%) and government (~11%) sectors globally.
For months, security researchers have suspected ShinyHunters of operating as an Extortion-as-a-Service (EaaS) group—partnering with other threat actors to extort victims and taking a cut of the ransom, much like a ransomware affiliate model. This theory gained traction after multiple breaches, including those at Oracle Cloud and PowerSchool, were extorted under the ShinyHunters name, despite the group not directly claiming the intrusions.
In conversations with BleepingComputer, ShinyHunters admitted they often act as brokers for stolen data, typically receiving 25–30% of any extortion payment. With the launch of their public data leak site, they now appear to be offering this service openly.
In addition to Red Hat, ShinyHunters is currently extorting S&P Global on behalf of another threat actor, who claimed responsibility for a February 2025 breach. While S&P previously denied any compromise, ShinyHunters has now released sample data and set an October 10 ransom deadline. When asked for comment, S&P Global declined, citing disclosure obligations as a U.S.-listed company.
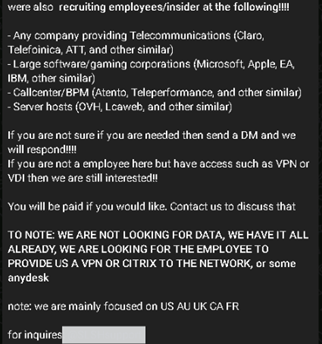
The Scattered LAPSUS$ Shiny Hunters posted an open recruitment message on their Telegram channel seeking insider access from employees at high‑revenue organizations — explicitly targeting sectors such as telecommunications (Claro, Telefónica, AT&T, etc.), large software and gaming firms (Microsoft, Apple, EA, IBM, etc.), call center/BPM providers (Atento, Teleperformance, etc.), and server hosts (OVH, Locaweb, etc.). The post makes clear they’re not after data (they claim to “have it all already”) but want persistent network entry — VPN/VDI/Citrix access, Active Directory capabilities, Okta/Azure/AWS privileged access — and offer payment for willing insiders. They encouraged uncertain candidates to DM them, said non‑employees with VPN/VDI access are also of interest, and noted a primary focus on targets in the US, AU, UK, CA, and FR. This brazen solicitation underlines their shift toward insider‑enabled intrusions to support extortion operations.
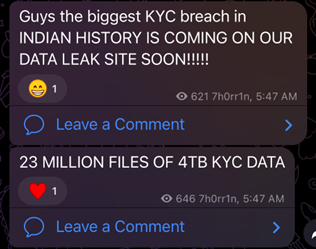
As of October 8, SLSH Group posted in their Telegram channel that they have in possession a large KYC dataset pertaining to Indian citizen. There was no further evidence shared and hence the authenticity of this claim remains uncertain at the time of writing this report.
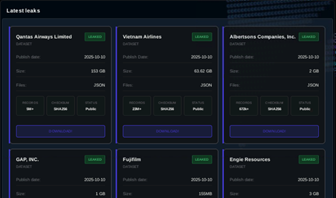
On October 11, Scattered LAPSUS$ Shiny Hunters (SLSH) disclosed intentions to launch a public EaaS offering. According to their statement, a portal and accompanying instructions will be made available. SLSH says the main advantage is that attackers can leverage the group’s name and reputation to increase effectiveness compared with anonymous attempts. Further information is expected. And they published the full leaked datasets of “Qantas Airways Limited”, “Albertsons Companies, Inc.”, “GAP INC.”, “Fujifilm”, “Engie Resources” and “Vietnam Airlines” on their darknet site, likely after negotiations broke down or ransom demands were rejected.
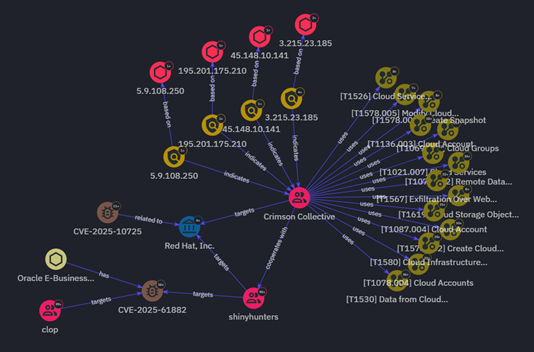
Contextualization
Seqrite Threat Intelligence (STI) offers complete correlation related to these groups along with proper enrichment and context on victimology, TTPs, vulnerabilities and more:
Conclusion
The rise of Scattered LAPSUS$ Hunters marks a new phase in cyber extortion, one driven by publicity, social engineering, and collaboration rather than pure technical skill. Their blending of tactics from LAPSUS$, ShinyHunters, and Scattered Spider reflects a broader shift toward loosely connected extortion alliances that thrive on chaos and visibility.
The use of leaked exploits like the Oracle E-Business Suite zero-day shows how quickly threat actors can weaponize public tools to amplify impact. Attribution remains blurred as groups share infrastructure and code across open platforms. This campaign reinforces that people, not just systems, are the weakest link. The best defense now lies in strong access controls, multi-factor authentication, continuous threat monitoring, and user awareness. These hybrid attacks prove that modern cybercrime is as much about psychological pressure and reputation damage as it is about technical compromise.
- Rotate all credentials and service accounts across Oracle, Discord, and third-party systems and follow Red Hat guidelines issued in the advisory.
- Patch all systems immediately and isolate any unpatched servers.
- Revoke and regenerate default auth tokens, API keys, session cookies, digital certificates (CER files) and private keys.
- Audit and clean all configuration files to remove hardcoded credentials or tokens.
- Implement continuous secret scanning in code and config repositories.
- Restrict admin and service access using least-privilege and just-in-time models.
- Enhance SIEM and EDR/XDR monitoring to detect credential or token misuse.
- Assess and secure third-party vendors; require SOC 2 or ISO 27001 compliance.
- Conduct a full data exposure analysis to confirm scope and impact of leaked data.
- Rebuild or restore compromised systems from clean backups if integrity is uncertain.
- Update the incident response plan to include leaked config, token, and certificate scenarios.
- Notify affected users or partners and comply with disclosure regulations.
- Enable continuous vulnerability scanning and scheduled credential/key rotation.
- Monitor dark web sources for leaked configs, tokens, or certificates.
- Train employees to recognize phishing, credential theft attempts and how not to fall into the vishing trap.




