From launching a DoS attack to phishing and pharming, leading to business and productivity loss, reputational hazard, financial and legal implications, DNS poisoning can have a lasting impact.
DNS, or Domain Name Servers, are used to convert human friendly web addresses such as Google.com and Facebook.com to their corresponding IP addresses that machines understand, and vice versa.
DNS poisoning, or DNS cache poisoning, happens when an Internet server’s DNS table is corrupted by changing the web addresses to point to rogue websites. There are multiple ways to transmit this – spam emails, images or banners within emails, malware and spyware that resides in computers and other nefarious codes that get installed in a user’s machine.
DNS cache poisoning is done by changing/adding records in the resolver caches (server used to resolve IP addresses), either on the client or the server. This ‘poisoning’ results in a DNS query for a domain throwing back an IP address for an attacker’s domain instead of the actual domain. See figure 1.1.
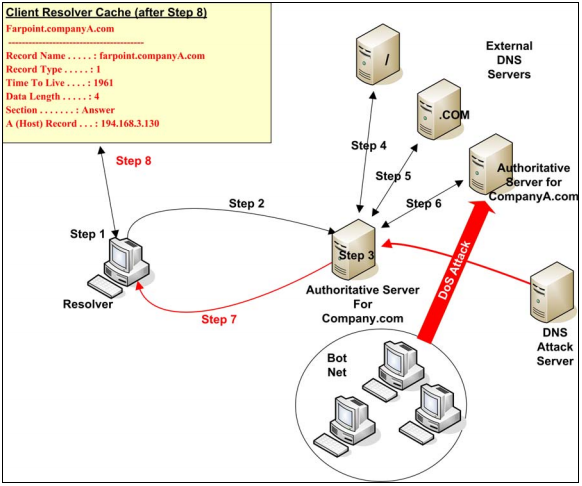
Figure 1.1: DNS Cache Poisoning
Who is susceptible to DNS attacks?
Any system that is configured to run DNS could be a possible target, including:
- DNS appliances
- Windows systems
- Unix systems (BIND), any device capable of proxying DNS lookups algorithmically
Additionally, the inbound network transport infrastructure is also at risk when such attacks occur because of the volume of traffic generated.
Perils of DNS attacks
Common practice these days is to have a second party act as DNS server. This second party acts as the slave and transfers information to the invisible primary DNS. In this case, the attacker poisons the entire zone between the primary DNS server and the slave, acting as the authoritative information parser. The impact here is much greater than a single PC being affected. The poisoned information is propagated to every DNS lookup that happens and no one will be able to access the victim’s domain.
Key perils of DNS attacks are DoS and DDoS attacks (the inbound network transport infrastructure is put at risk because of the volume of traffic generated) and phishing and pharming attacks.
Phishing happens when an attacker sends an email that appears to be from a bank or a trusted source and tricks the recipient into accessing a malicious website to get sensitive information such as usernames, bank account details and passwords. Attackers build the spoof website similar to the real one, and disguise links so that the unsuspecting user is not alarmed.
For example, www.onlinebank.com can be spoofed as www.0nlinebank.com (letter o is changed to zero).
According to experts, India is the fourth most favorite target of cyber criminals when it comes to phishing attacks. This is also evident by the number of cyberattacks hitting the country, which has scaled exponentially in 2013. Findings by the Indian Computer Emergency Response Team (CERT-In) on number of Indian websites defaced and hacked in 2013 (in just 4 months) supports the statement too:
- August – 4,191
- July – 2,380
- June – 2,858
- May – 1,808
While phishing and pharming are related, the latter is when the attacker tricks the DNS server into caching incorrect entry for a domain name of a trusted site, such as an online bank web address. When the unsuspecting user types the domain name on the browser, the DNS server provides the cached record of the impostor site – thus pharmed via DNS cache poisoning.
Such an attack allows the hacker to route any Internet-based application (HTTP, FTP, SMTP, DNS, POP3, IMAP, SSH) that is based on DNS names, instead of IP addresses, to steal usernames and passwords, corrupt business emails, and cause disruption in business resulting in loss of productivity, at the very least.
Preventing DNS attacks
DNSSEC or DNS Security Extensions are a set of IETF (Internet Engineering Task Force) standards created to address vulnerabilities in the Domain Name System (DNS) and protect it from online threats. DNSSEC digitally signs records in a response message – authenticating the identity of the name server and validating the response. Name server also sends a public key of the zone to verify the digital signature.
Challenge in DNSSEC implementation is that it is complex, and on a voluntary basis, resulting in low adoption rate. Another challenge is that DNSSEC provides only one-way authentication – no authentication of the client. Thus, it cannot prevent use of a name server for bandwidth consumption DoS attacks.
A solution to this could be to use digital signatures both at the server and client end. The client and server could also encrypt the messages using two-way SSL.
Some organizations use a basic firewall configured to only allow certain connections from trusted sites and partner VPNs. Every other connection is dropped by the firewall. Experts and practitioners advise that internal Intrusion Prevention Systems (IPS) and packet analyzers will help to protect from DNS attacks.
